Executive summary
In early November, Mad Devs received reports of suspicious messages claiming to offer individuals work and profit-sharing opportunities with our company. We discovered these messages were a front for a scam in which users deposited a certain sum to a cryptocurrency wallet for a criminal group. Further investigation revealed the source of the website, after which we reported these resources to the relevant providers and groups. Our team also discovered a large-scale criminal enterprise that has stolen around $35 000 000 (millions!) since 2022.
It is no secret that the Internet plays a critical part in our lives today; however, it contains many risks, too, such as scams, phishing, and other cybercrimes. These threats affect everyone, from individuals to companies, and Mad Devs is no exception.
We recently encountered a situation where scammers used our company’s name with malicious intent. In this article, we want to share our experience and tell about the steps we took to reduce the harm, from our investigations to outreach and communication with other companies and Internet services.
Before we begin, we would like to issue a friendly reminder to never open or respond to e-mails and messages from the telephone numbers and e-mail addresses mentioned in this article. They are controlled by scammers and cybercriminals with no affiliation to Mad Devs.
Background
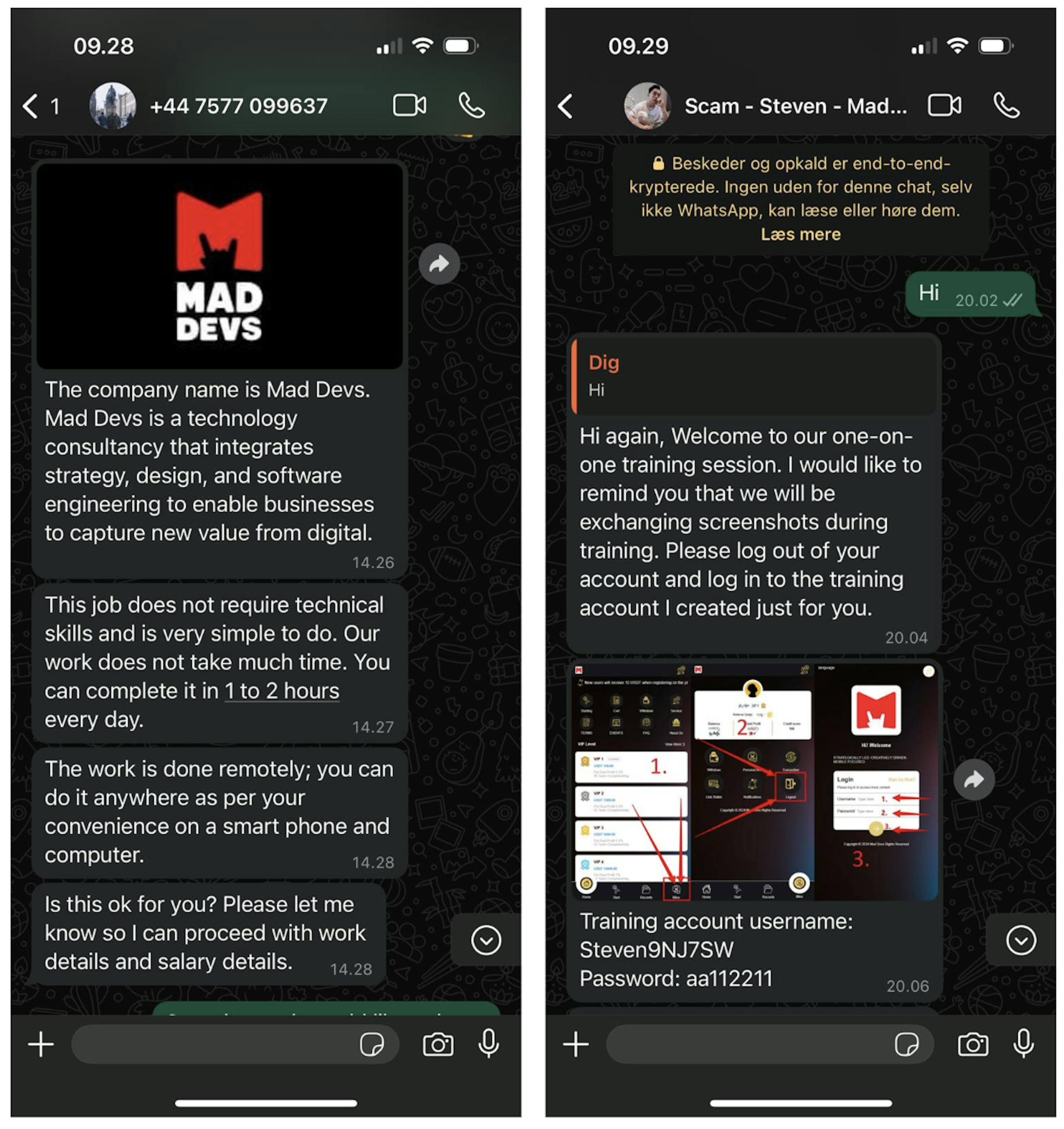
In early November 2024, our company began receiving reports of suspicious activity under our name. Messages with "tempting offers" from individuals named Steven and Luna were sent via WhatsApp and email to various individuals. Posing as employees of Mad Devs, they offered job and training opportunities and consultations in exchange for cryptocurrency and a profitable partnership.
Here are some examples:
E-mail:
| Maddevs is an International company located in London. Our mission enables us to go beyond the optimization of app development and provide competent reviews on Google Play/App Store, provide satisfaction, and improve your business processes online. Our working hours are from 11am-11pm UK time. You can complete the work using your phone/laptop at any time during this time. When you are familiar with our work, you can complete it in about 30-1h minutes every day. Okay so basically, we help apps that partner and cooperate with the company optimize their apps. Our job here is as a Data provider. Our main responsibility is to "SUBMIT" the assigned tasks using the Maddevs workbench. Each click uploads real data, optimizing apps with our network data. This boosts exposure, rankings, downloads, sales, and genuine reviews. The company generates revenue by optimizing the applications from its partnered companies and supporting multiple start-up developers in enhancing their application to the system. This business model is similar to B2B (business-to-business). |
We analyzed these messages and discovered several websites that had copied our corporate style. The addresses of these resources are as follows:
- https://www.maddevs-app.com/
- https://www.maddevsappsglobal.com/
- https://www.maddevsapp-global.com/
- https://maddevsapps.com/
- http://maddevsglobal-apps.com/
As well as others similar to these.
Here are the numbers the scammers used to contact applicants:
- +44 7475 094440
- +44 7473 579535
- +44 7491 441660
- +44 7832 302483
- +44 7491 343792
- +44 7577 099637
- +44 7446 344577
As we received more messages from individuals who had received these offers, it became clear that this was a complex issue that needed to be addressed. We decided to investigate these resources with the aim to, ideally, eliminate the threat they posed to us and others or, at the very least, reduce the harm they could cause.
Investigation
We began our investigations with a focus on three areas:
- Identifying the method of fraud
- Understanding the mechanics of the scan
- Determining the information channels used by the scammers
The goal was to evaluate the true scale of the threat posed by these impostors. Sometimes, scam sites are associated with larger criminal enterprises, such as phishing campaigns, malicious software, or organized cybercrime.
Finding the registration location of imposture DNS records
Firstly, we discovered the service used to register these resources: CloudFlare. After submitting a complaint with clear evidence of fraud, CloudFlare began blocking the malicious websites.
Studying the software
In the short amount of time available, we studied the software that was accessible through these websites. The software had identical cdn-cgi directories and files, which hinted us they were copies of one application.
We sent a large amount of HTTP requests, which returned a 522 “Connection timed out” error. Then, the same requests were successfully sent and handled from another IP address, indicating that these resources had a blacklist of IP addresses or a time-out mechanism.
Fraud mechanism
Thanks to information from users and our own research, we uncovered how the scammers operated. Their lucrative offer required applicants to deposit an amount of cryptocurrency to a designated wallet. Then, the applicants registered a special training account on their website to complete tasks. The more tasks they performed, the larger the commission they would receive that would be added to their initial deposit.
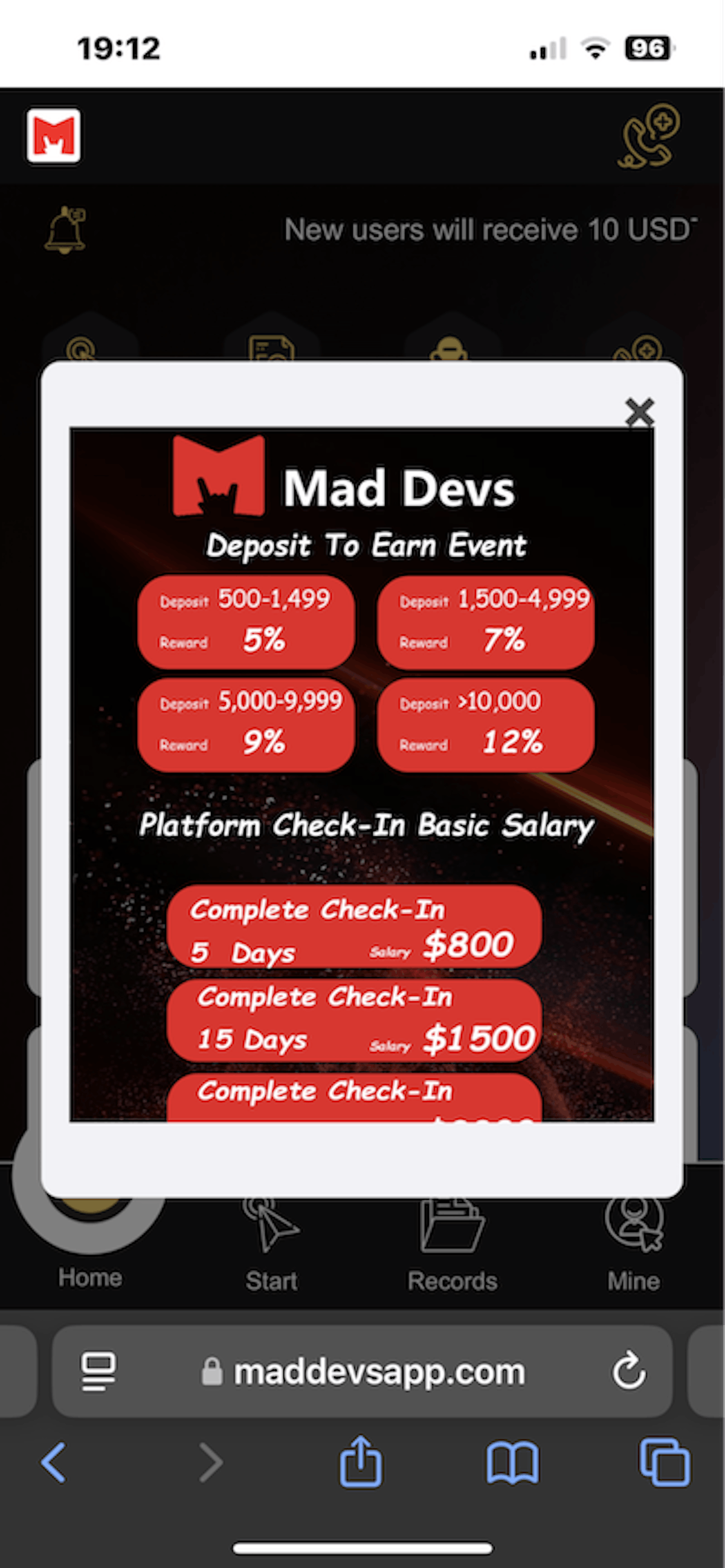
These resources sent users to the following endpoint: https://<malicious domain>/index/user/kefu. On this page, they could begin communicating with a "support specialist" who would provide them with the address of the wallet for an EVM-compatible blockchain.
Further scanning revealed this endpoint: https://<malicious domain>/index/user/details?id=<number>. It returned interesting content:
/index/user/details?id=1- a description of the transfer scheme for potential users (in Arabic)/index/user/details?id=7- creates an error that returns technical details on the product
IP address and location
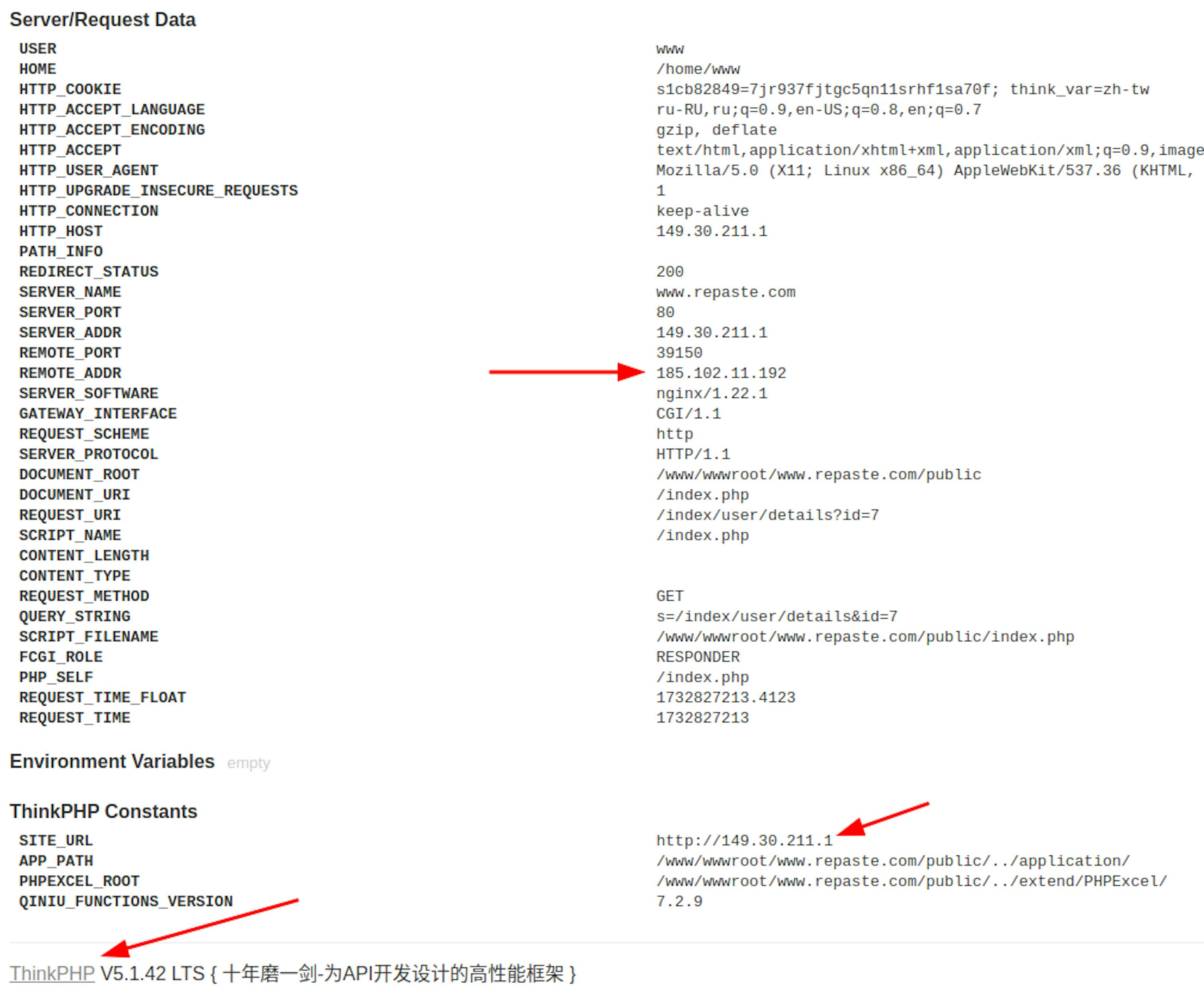
Closer inspection allowed us to identify an IP address:
SERVER_NAME 149.30.211.1 SERVER_PORT 80 SERVER_ADDR 149.30.211.28 REMOTE_PORT 33644 REMOTE_ADDR 172.68.35.141 SERVER_SOFTWARE nginx/1.22.1
A search showed that the address has two potential locations, the US and Hong Kong.
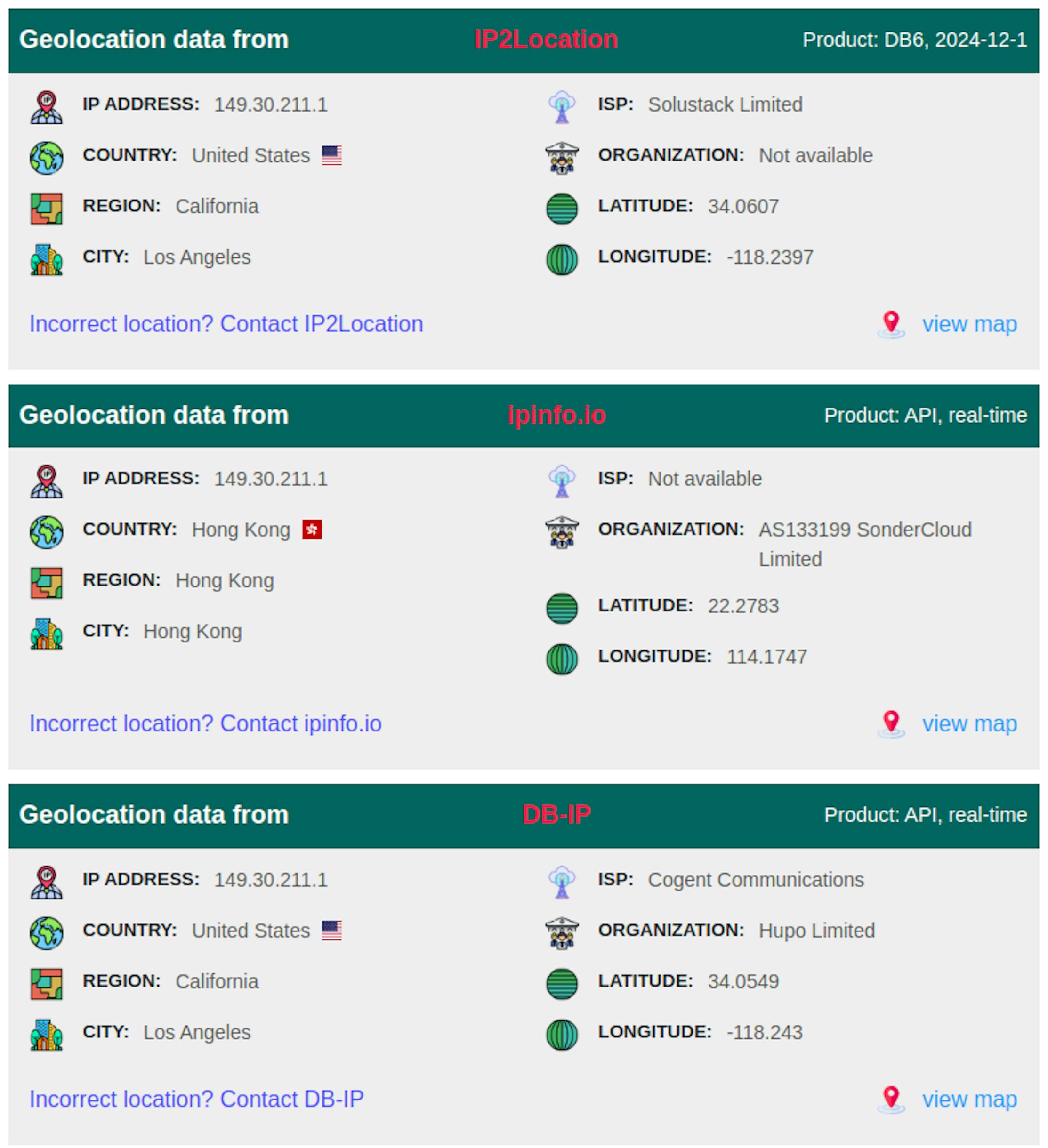
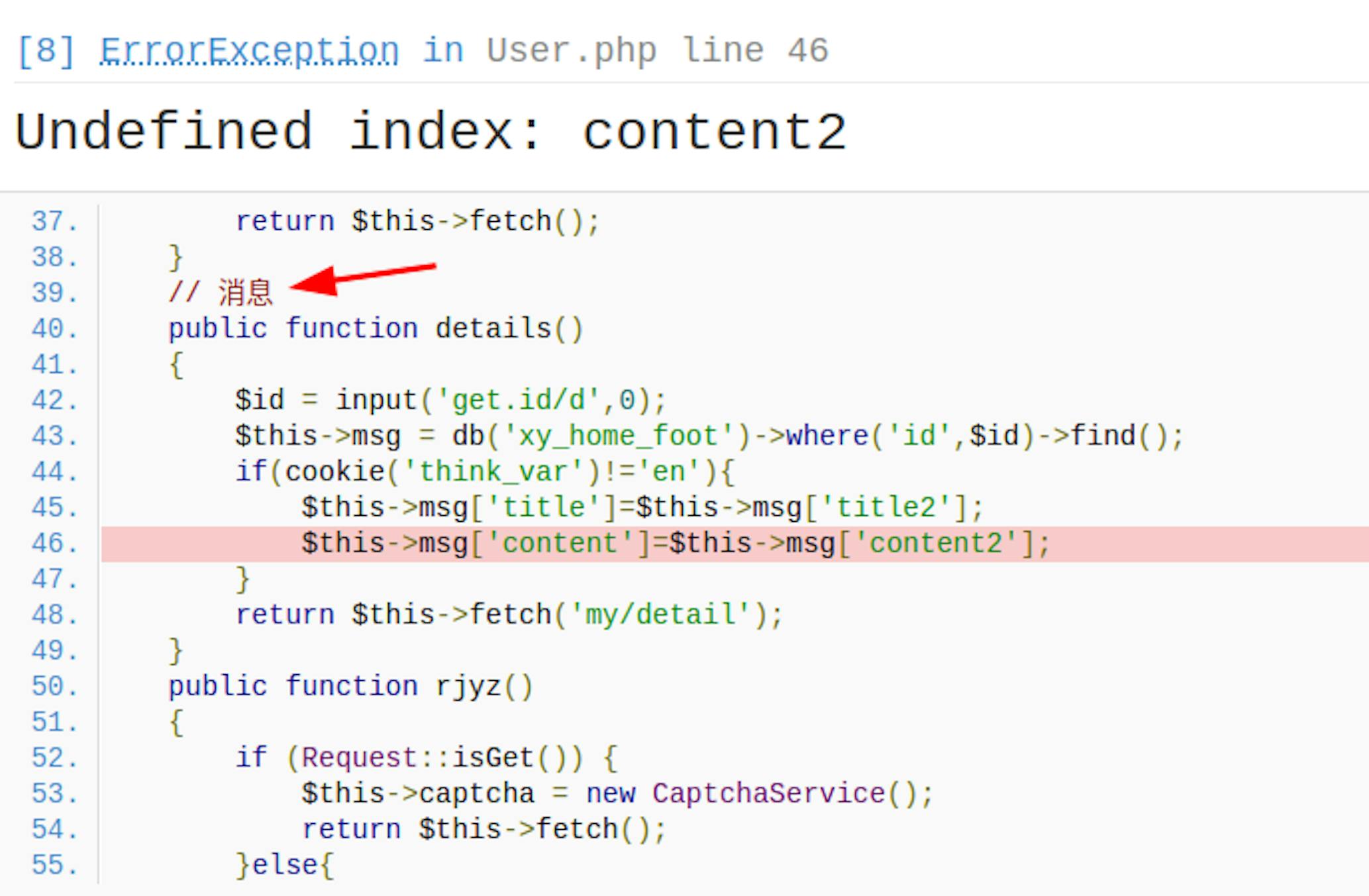
During our examination of the software and resources, we noticed comments to code and other notes written in simplified Chinese, which provides some certainty that the trail leads to Hong Kong.
Admin panel
Our investigators later found an admin panel at this address: http://149.30.211.1/admin/login.html with code that corresponds to our earlier discoveries, including the use of Chinese in the comments:
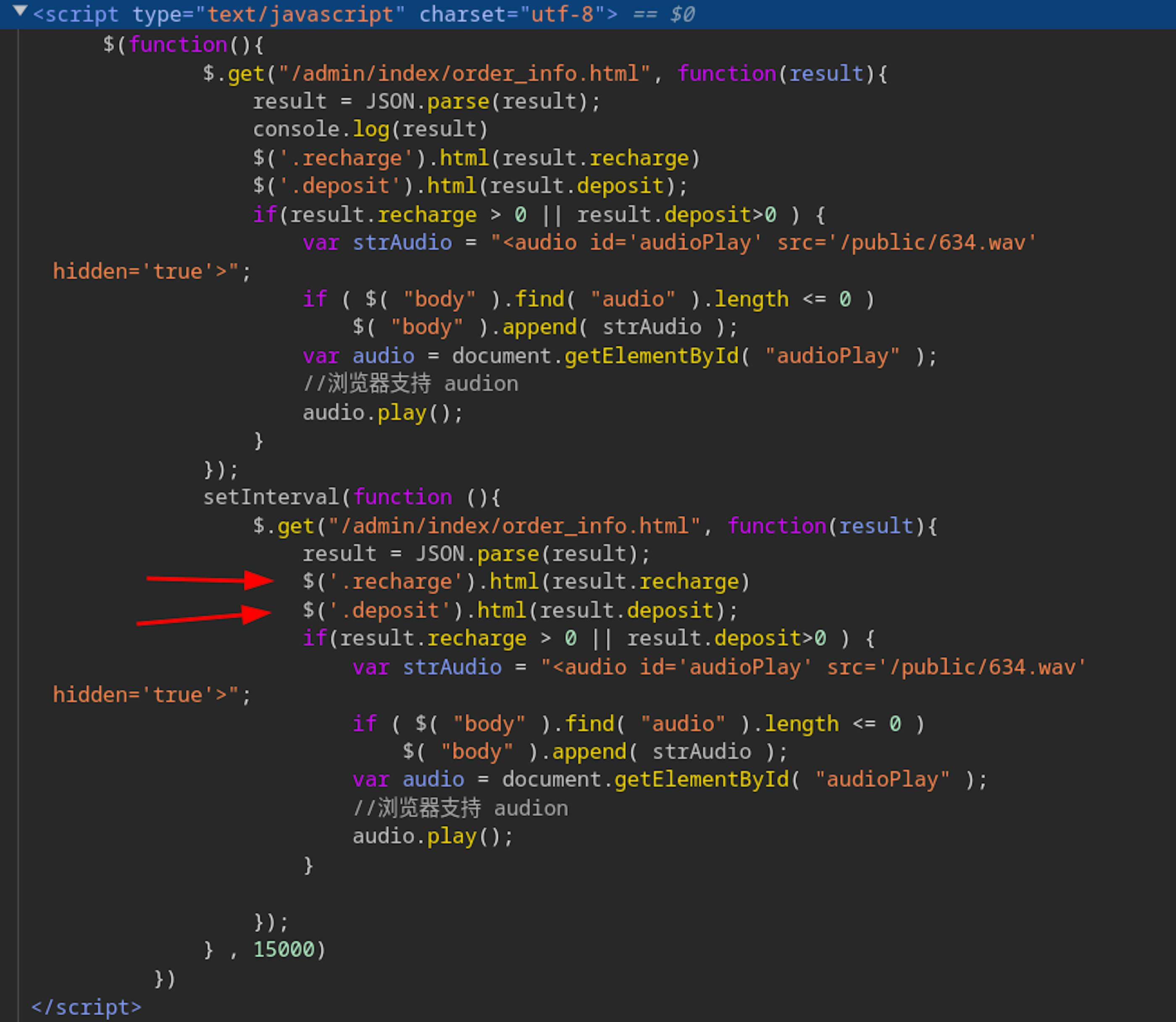
One point caught our attention in particular. We noticed that the website's users saw the word "Deposit" on their screens (see screenshot above), but the code also contains the word "Recharge." This indicates a poor level of professional competence that is common among malicious domains. They also didn’t hide part of the client logic in their code when receiving new transactions.
Blockchain discoveries
A separate part of our investigation involved analyzing the blockchain transactions, during which we uncovered a large-scale network of accounts that have existed since the middle of 2022. The criminal group behind the scam uses a simple template for transferring stablecoins and extracting the amount in the blockchain's native currency.
The template works as follows:
- The phishing website offers users the opportunity to deposit a small amount of 50 USDC/USDT to the Polygon network.
- The user then contacts support to transfer the amount.
- A one-time address is given for the transaction. A wallet like this exists for several minutes or up to several days.
- The scammers then transfer native currency to the new address from a previously used wallet to pay for withdrawing the stolen funds.
- The user transfers the sum to the temporary wallet.
- The cycle is repeated once a set amount has been gathered in the wallet.
To work, this scheme relies on the companies it impersonates initially being unaware of the scam that occurs under their brand. Mad Devs became one of a dozen companies the criminal group used to steal funds.
Our team then began to study the funds moving through this criminal group. Using reverse analysis methods on the blockchain's native currency (POL/MATIC), we found one of the first addresses the group used that had signs of real activity:
- Deposits and exchange operations
- Staking
- DeFi participation
Here is an extensive analysis of one of the first wallets in the chain:
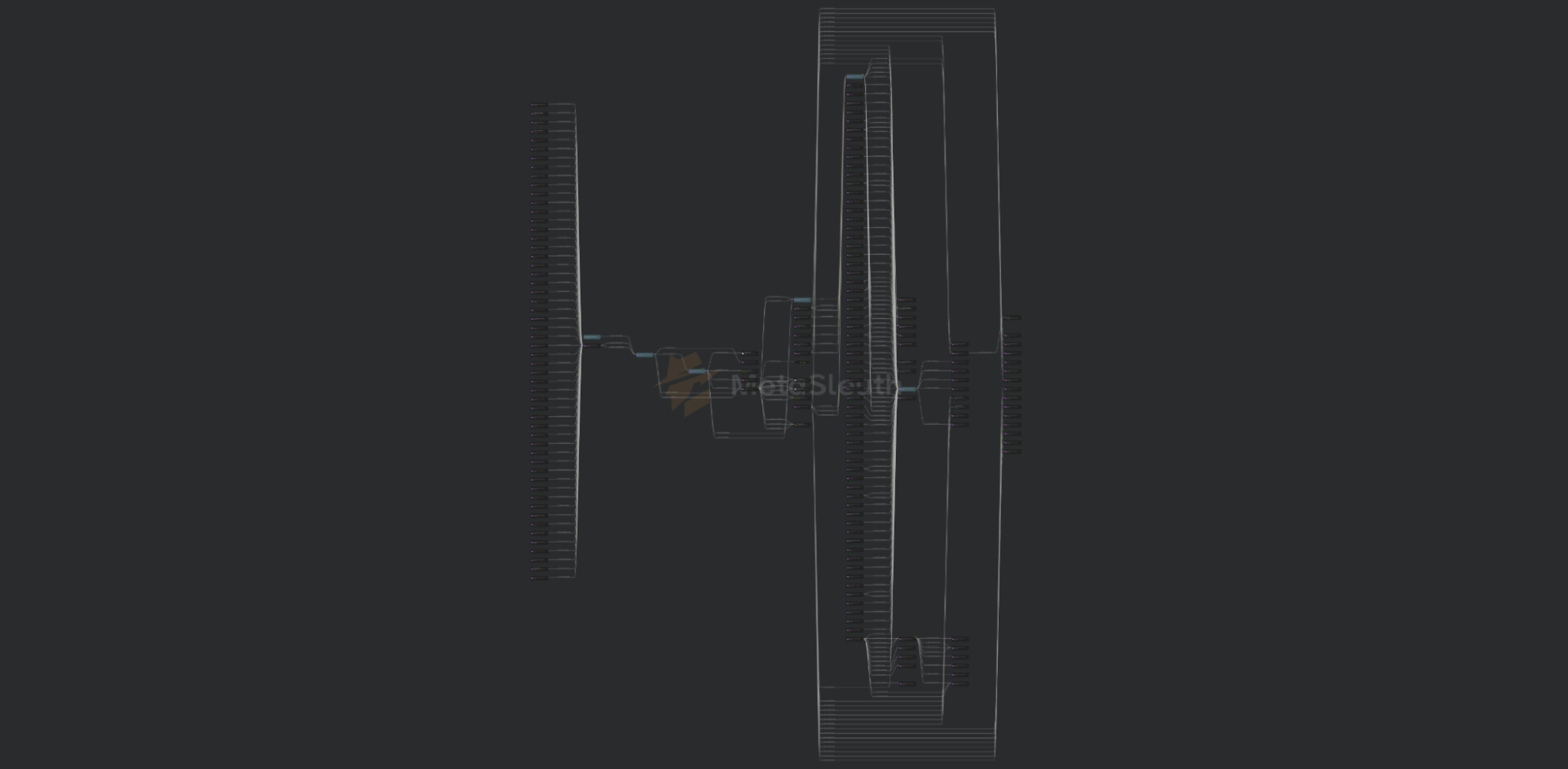
(Note: The image has been compressed. The original is available at this link. Registration may be required.)
Based on the wallet data provided by affected users, we were able to identify one of the source group’s source addresses, which allowed us to understand the operation’s scale by connecting the transfer of funds between the criminals’ wallets. As of 16 December 2024, the criminal group has stolen around $35M since creating the source wallets.
Our investigations also revealed data to prove the connection between these wallets and the criminals. The data is available here.
After reviewing the transactions, it became clear that the criminals use a simple method of extracting the funds through hot wallets on central exchanges, such as:
- Binance
- Crypto.com
- Bitget
- MEXC
Next steps
Blocking IP addresses
With this evidence, we then filed complaints to the resources hosting these IPs. Cloudflare had blocked them based on their DNS records, but users could still access them through an IP. The hosts were:
- SoluStack
- SonderCloud
- Cogent Communications
We also took steps to report the phishing to various blacklists:
At this point, the scammers may have moved to other addresses; however, these particular resources are no longer available to them.
UpAnalytics
During our investigations and reporting of the scammers using Mad Devs’ name, we uncovered a similar effort to scam users by impersonating the company UpAnalytics. Our team has contacted them to report our findings and investigations and to offer any assistance to counter the effects of the criminals.
Conclusions and results
Mad Devs wants to assure past, present, and future clients and employees that we take these situations seriously. If any individuals or groups use our brand in a malicious manner, we will fight their attempts. Our aim is to remain transparent for everyone.
Remember, don't send money to anyone without understanding who they are and where the funds are going. The Internet can be an unfriendly place with creative criminals.
We are happy to report that our investigations and actions have reduced the effect of this criminal group by blocking at least one of their resources. We recommend contacting internet providers and DNS services with complaints if individuals or companies encounter similar situations. These businesses do respond.
Mad Devs is committed to making the Internet a safe place, and we ask any individuals and companies with information regarding this criminal group to contact us and work together on our investigation.










