Cybersecurity is becoming increasingly relevant in an era of ever-increasing digital assets and widespread digitalization of corporate processes. Key players in this context are the red and blue teams. In this article, we will explore the fundamental principles of their operation, methods of interaction, and their value for the cybersecurity of organizations.
Red team vs. Blue team vs. Purple team
The red team specializes in simulating real threats and attacks to identify vulnerabilities in defense systems. The blue team focuses on analyzing such attacks and developing methodologies for their mitigation and prevention. The purple team aims to facilitate effective interaction between offensive and defensive elements, analyze the results, and suggest measures for optimizing mutual strategies and tactics.
Importance for cybersecurity
The collaborative work of the red and blue teams transforms cybersecurity approaches from static measures into a dynamic, continuously updated system. The purple team coordinates these efforts, and ensures effective communication and knowledge transfer between the red and blue teams, thereby enhancing the overall effectiveness of a cybersecurity strategy.
This allows corporations not only to deflect but also anticipate threats, thereby maintaining continuous protection, safeguarding their assets, and ensuring the resilience of work processes.
However, we will focus on the red and blue teams as the foundation of cybersecurity and an established model for its provision.
Red team (Offensive security)
The role of the red team is to simulate real-world attacks on a company's systems, networks, or applications, aiming to identify vulnerabilities that could be exploited by malicious actors.
Red team techniques include spear phishing, ransomware attacks, identity spoofing, session hijacking, and injection attacks. Additionally, they utilize social engineering and psychological manipulation to take advantage of human weaknesses.
Let's delve into various aspects of the red team's work, and discuss their core expertise, security methods, real value they bring to organizations, and challenges in collaboration with the team.

Areas of expertise of the red team
The red team focuses on four key areas:
- Ethical hacking. Simulating attacks on systems with the consent of the owners to identify vulnerabilities and test security measures.
- Threat and risk analysis. Investigating the types of attacks the system is exposed to and assessing the likelihood of their successful execution.
- Code testing. Analyzing the source code of website architectures and applications for vulnerabilities that could be exploited.
- Reporting and recommendations. Preparing detailed reports on identified vulnerabilities and suggesting measures for their mitigation.
Security testing methods
The red team employs a comprehensive set of techniques and tools for security testing. These can be used individually for examining different layers of the system, but they can also be combined for multi-layered testing depending on the specific needs of a business and the peculiarities of a given system.
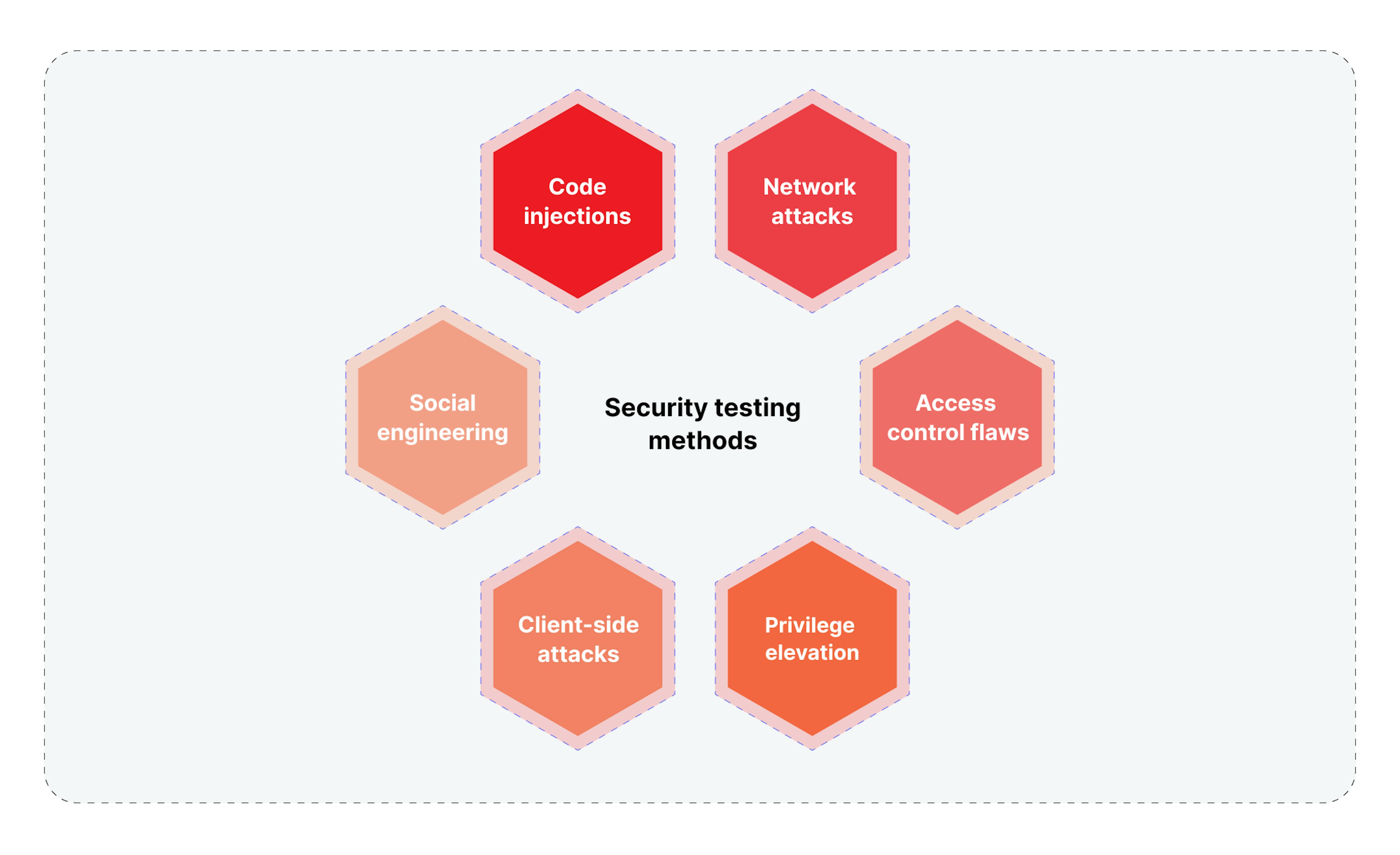
Code injections
Here, the red team focuses on identifying weaknesses in input data validation and filtering. Through various test code scenarios, the team assesses whether unexpected commands can be executed within the current system. This helps evaluate how well the system is protected against attempts to compromise data integrity or gain full control over the server. Discovered vulnerabilities could serve as entry points for attackers, enabling them to launch ransomware, spread malware within the network, or even remotely initiate processes that could effectively paralyze corporate operations.
- SQL injections. Manipulating SQL queries for unauthorized database access.
- OS command injections. Embedding and executing operational commands in the system.
- LDAP injections. Distorting LDAP queries to bypass access control systems.
- XPath injections. Injecting code to manipulate XML documents.
- Server-side template injection. Injecting malicious code through server templates.
Network attacks
Here, the read team focuses on methods to analyze and monitor the network usage traffic in order to determine how difficult it is to gain unauthorized access or falsify data in real time. Even minor delays in network transmission can be exploited to gain unauthorized access to financial transactions or control over corporate infrastructure.
- Man-in-the-Middle (MitM) attacks. Intercepting and modifying traffic between two parties.
- DoS/DDoS attacks. Overloading network resources to render them inoperative.
- Network scanning. Identifying active devices and open ports on the network.
- Server-side request forgery. Forcing the server to execute unwanted requests.
Access control flaws
The red team's testing is also about the detailed analysis of authorization systems, which includes two-factor authentication mechanisms, password policies, and role segregation. The process helps identify vulnerabilities that could be exploited to access restricted sections of the system or databases containing sensitive information. This could lead to severe consequences, such as intellectual property theft, financial manipulation, or even blackmail based on stolen data.
- Brute-force attacks. Password guessing through multiple login attempts.
- Insecure direct object references. Unauthorized access to objects due to flaws in the access control system.
- Open redirects. Redirecting users to malicious websites.
- Session fixation. Capturing and using another user's session.
- Parameter tampering. Manipulating request parameters to bypass restrictions.
- Subdomain takeover. Capturing unused or improperly configured subdomains.
Privilege elevation
In this case, the red team seeks ways to circumvent system restrictions, for example, by exploiting vulnerabilities in operating systems or services. Success in this area provides attackers with a wide range of threatening possibilities. It includes the ability to start and stop services, alter critically important system settings, and potentially destabilize the entire corporate infrastructure or even orchestrate its complete takeover.
- Privilege escalation. Utilizing vulnerabilities in the system or application to gain control over initially inaccessible resources.
- Race condition. Exploiting the time window between condition checks and operation execution.
Client-side attacks
The red team also focuses on analyzing web browsers, plugins, and other client software. The main goal is to identify vulnerabilities that can be used to execute malicious code on end-user devices. This can range from personal data theft to installing malware, which may, for example, encrypt user files for subsequent ransom.
- CSRF (Сross-site request forgery). Performing unwanted actions on behalf of the user.
- Clickjacking. Manipulating the user interface to perform unnoticed actions.
- Cross-site scripting (XSS). Injecting scripts to manipulate web pages.
- File inclusion. Embedding external files into the page code.
- HTTP response splitting. Manipulating HTTP responses to execute code or steal data.
Here, the red team uses psychological methods to manipulate employees to obtain confidential information or system access. This can vary from simple strategies, such as "spoofing" emails from high-ranking individuals, to complex scenarios where attackers may, for example, pose as technical support to install malicious software. Success in this area can lead to the theft of sensitive data, financial fraud, or even complete compromise of corporate systems.
- Spoofing. Imitating legitimate network participants.
- Phishing. Fraud is aimed at stealing credentials through fake web pages or messages.
- Zero-day exploit testing. Exploiting unknown vulnerabilities before their official discovery and patching.
Thus, the red team simulates possible actions of real attackers to identify vulnerabilities and provides a comprehensive understanding of how attackers can compromise system integrity and what measures are needed for security.
Value red teams bring to companies
Let's consider the direct and real value that red teams provide to businesses of various sizes.
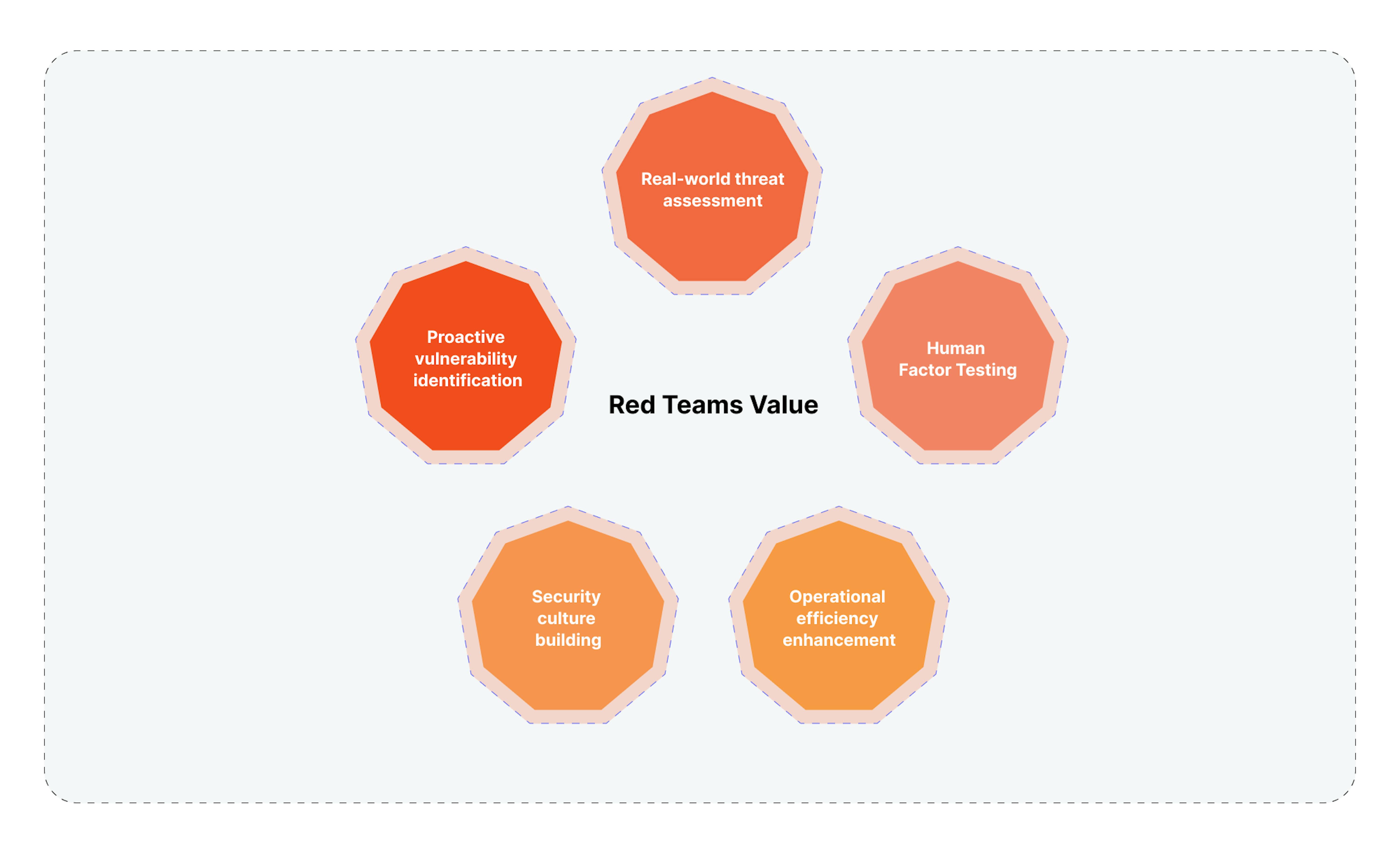
- Proactive vulnerability identification
Red teams identify weak spots in systems, preempting potential actions by malicious actors. This is not just a data leakage prevention measure but also a tool to avoid reputational losses and financial penalties. Code scanning, configuration analysis, physical security testing, and more are all part of a comprehensive strategy aimed at risk minimization. - Real-world threat assessment
Red teams go beyond the basic list of vulnerabilities. They analyze each discovered vulnerability in the context of the real world, considering current threats and possible attack scenarios. This allows companies to focus on eliminating the most critical threats and real risks. - Human factor testing
Red teams use social engineering methods to assess employee awareness levels. This is not just an attentiveness check; it's a comprehensive analysis that helps identify what educational programs or changes in corporate culture can improve overall security. - Operational efficiency enhancement
The knowledge of what systems and processes are most vulnerable allows companies to optimize resource allocation. This saves the budget and improves overall productivity, enabling resource reallocation where it will have the most impact. - Security culture building
Regular audits and tests from red teams elevate the security level and stimulate the development of a security culture within the organization. This makes every employee an active participant in the security process and helps create a standard system of values and principles that strengthens the organization as a whole.
Overall, red teams provide a comprehensive threat analysis, from identifying technical vulnerabilities to assessing the human factor, offering invaluable data for continuous improvement and adaptation of security strategy. This allows businesses to always be in a state of countering new threats and maintaining the current security status of their systems.
Challenges in working with red teams
Red teams can bring not only advantages but also specific challenges that can be critical for a business.
Cost and resources
Investing in red teams is not just a financial matter. Yes, quality services cost money, but it also requires the time and effort of employees. They must actively collaborate with the team, provide necessary information, and analyze results. This can divert them from their primary work tasks, which is also a form of expenditure.
Operational risks
Conducting penetration tests and other audits may inadvertently disrupt critical business processes. Even with utmost caution, the risk of outages or temporary service unavailability always exists.
Communication issues
Clarity and transparency in communication with the red team are key success factors. Misunderstanding objectives, limitations, or methodology can lead to irrelevant or incomplete results, thereby reducing the effectiveness of the entire process.
Complexity in result analysis
After completing the tests, the data needs to be not just collected but also correctly interpreted. This may require specialized skills and tools for threat analysis, classification, and prioritization. Mistakes at this stage can lead to incorrect resource allocation for vulnerability remediation.
Psychological factor
External security checks can induce stress or even resistance among employees. This can affect the team atmosphere and requires a tactful approach to minimize negative impact.
Compliance with norms and standards
Different industries and jurisdictions have their own laws and standards concerning information security. This can complicate the selection of a suitable red team and add additional steps in the test preparation and execution process.
Therefore, working with red teams requires meticulous planning and attention to detail — from finances and operational risks to communication and compliance with standards. However, when properly managed, these complexities will allow you to maximize the benefits of collaborating with a red team while minimizing risks to your business.
Blue team (Defensive security)
The blue team focuses on protecting, monitoring, and improving the security of information systems to prevent breaches. They work to ensure that the organization's security measures are robust enough to withstand real-world attacks, often responding to threats in real time.
Blue team exercises examples involve conducting DNS research, performing digital analyses to establish a baseline of normal network activity, and configuring and monitoring security software to identify unusual or suspicious behavior.
After gaining a comprehensive understanding of the expertise, methods, specific values, and challenges of red teams, it's time to delve into the downside and learn about all of this concerning the blue team.
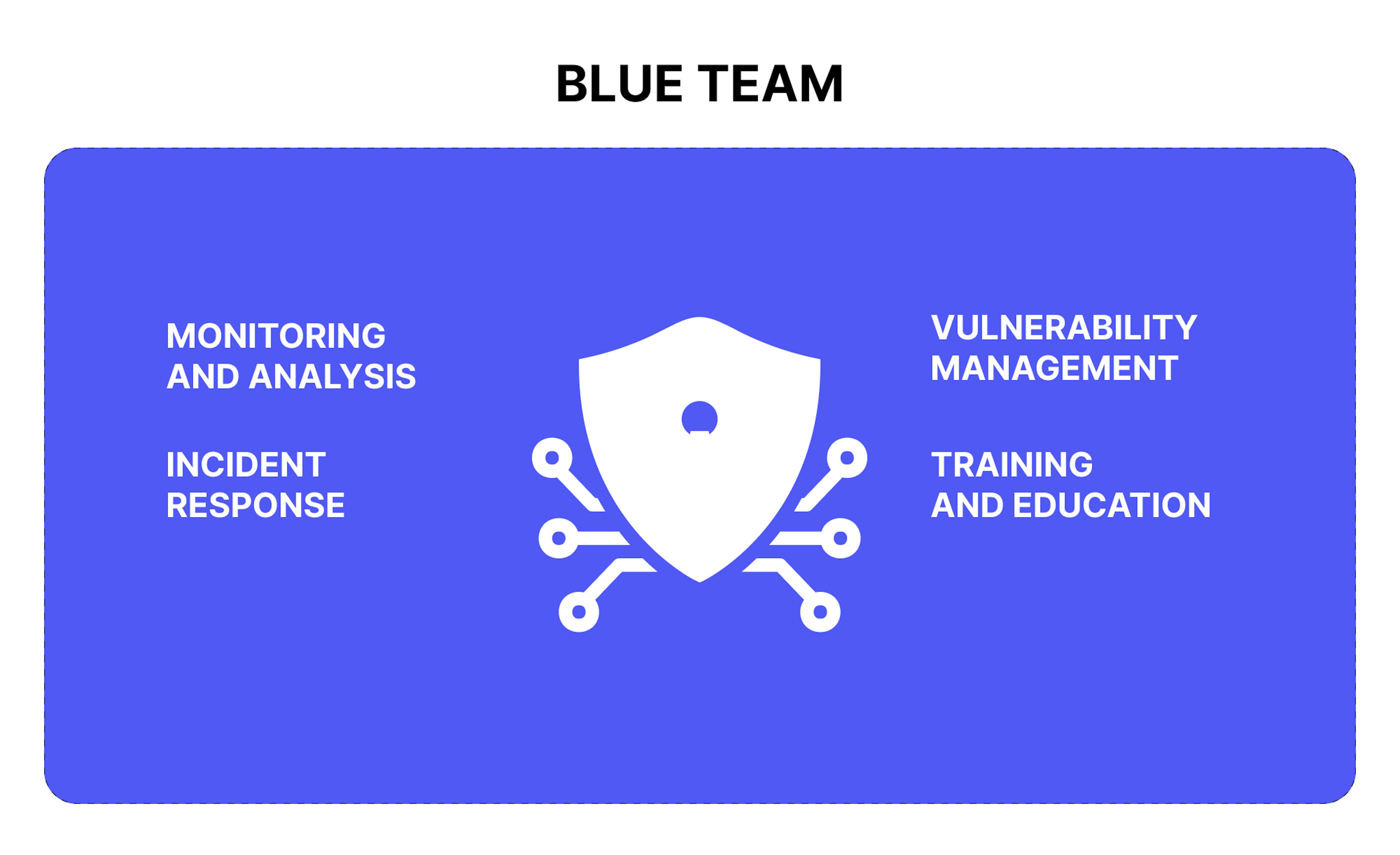
Areas of expertise of the blue team
The blue team focuses on four key areas:
- Monitoring and analysis. Continuous tracking of network traffic and system logs to identify anomalous activity and potential threats.
- Incident response. Procedures and methodologies for rapid and effective response to security incidents, minimizing damage, and restoring normal operations.
- Vulnerability management. A systematic approach to identifying, classifying, and remediating vulnerabilities in systems and applications.
- Training and education. Development and implementation of educational programs for employees on cybersecurity and awareness.
Security measures
Just like testing methods, security measures include a wide array of techniques and tools. These can be used individually or in combination, depending on the specific vulnerabilities of a system, the resulting potential risks, and their relevance to particular companies.

Endpoint security
Focuses on securing individual devices that connect to the corporate network. The blue team is responsible for installing, configuring, and monitoring antivirus software, intrusion detection systems, and other protective mechanisms on these devices.
- Antivirus software. Utilizes software to detect and remove malicious code.
- Intrusion detection systems (IDS). Monitors network traffic to identify anomalous patterns.
- Data loss prevention (DLP). Mechanisms for preventing the leakage of confidential data.
- Device control. Manages access to peripheral devices, such as flash drives.
Configuration audits
Also, the blue team regularly audits system and application configurations to ensure compliance with security standards. This includes checking access rights, network settings, and other parameters.
- Access control lists (ACLs). Verifies access control lists for files and directories.
- Security policies. Audits security policies for compliance with corporate and industry standards.
- Patch management. Checks and installs the latest security updates.
Authentication
They implement two-factor authentication to strengthen account security, adding an extra layer of verification to the standard password.
- SMS verification. Identity confirmation through SMS codes.
- Hardware tokens. Uses physical tokens to generate temporary codes.
- Biometric verification. Uses biometric data such as fingerprints or facial recognition.
Data locking and encryption
It uses various methods to ensure data confidentiality and integrity, including disk-level and file-level encryption, as well as restricting access to sensitive information.
- Disk encryption. Encrypts the entire disk to protect data in case of physical access to the device.
- File-level encryption. Encrypts individual files or directories.
- Database encryption. Encrypts databases to protect stored information.
Network segmentation
Network segmentation divides the corporate network into isolated segments to reduce the attack surface. The blue team is responsible for developing and implementing a segmentation strategy, which may include VLANs, subnets, and firewalls to control traffic between segments.
- VLAN (Virtual local area network). Isolates groups of devices within a single physical network.
- Subnetting. It divides IP address space into smaller, manageable blocks.
- Firewall rules for segmentation. Sets up firewall rules to control traffic between segments.
Logging and monitoring
The blue team collects, stores, and analyzes logs to ensure timely response to incidents and to detect anomalous activity. This includes security event monitoring, traffic analysis, and configuration audits.
- SIEM (Security information and event management). Centralized collection and analysis of security data.
- Traffic analysis. Monitors and analyzes network traffic to detect anomalies.
- Configuration audits. Regular audits of system and network configurations.
In this way, the blue team adopts a multi-layered approach to security, including data protection, account security, network infrastructure, and security policies, not only to eliminate the emergence of new vulnerabilities and reduce the risks from their detection but also to ensure timely response to incidents and maintain high-security standards.
Value blue teams bring to companies
Now, let's consider the specific value that blue teams bring to companies.
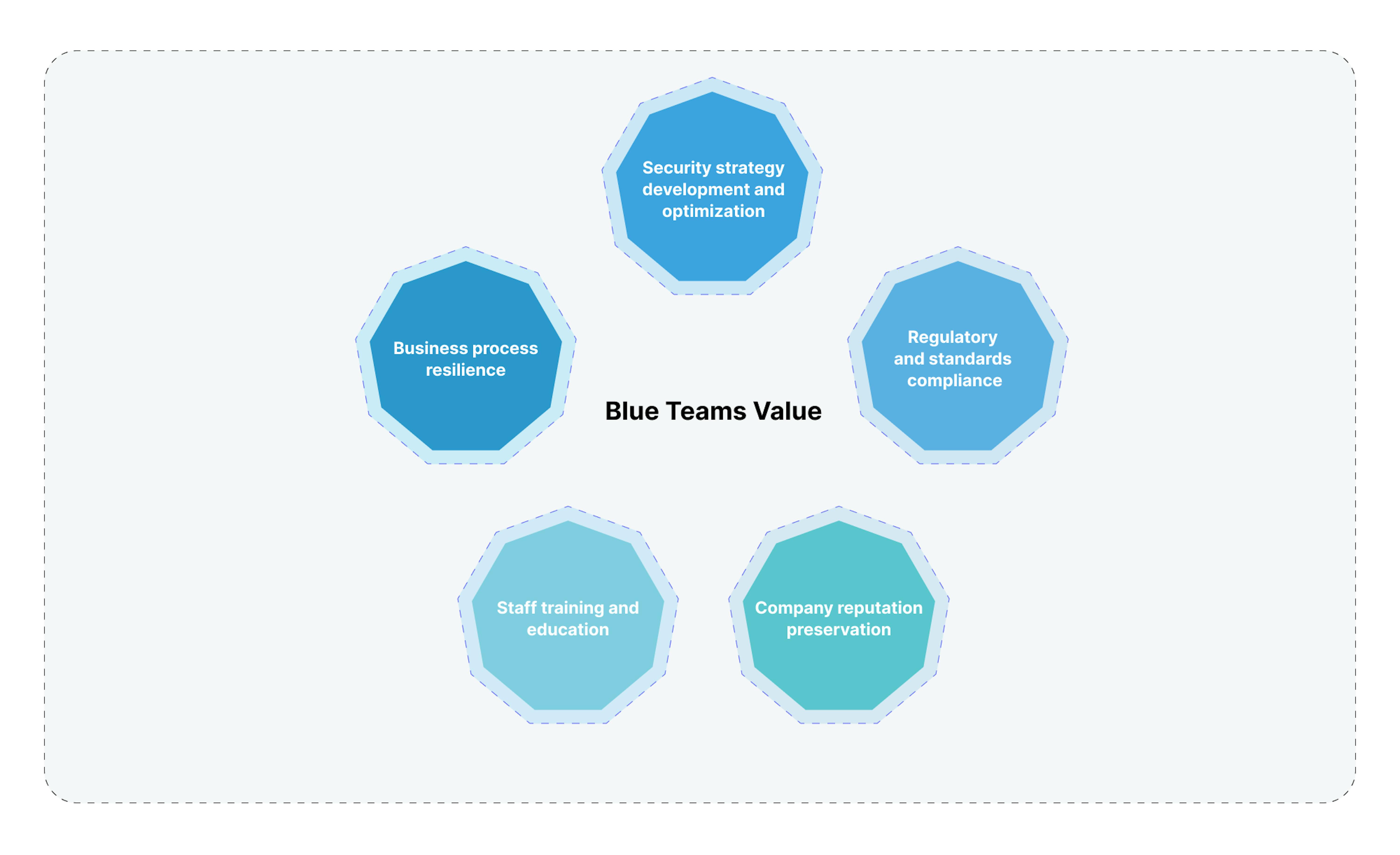
- Security strategy development and optimization
Blue teams can create and continually refine security strategies tailored to specific company needs and resources. This ensures the maximum effectiveness of security measures while minimizing costs. - Regulatory and standards compliance
Blue teams ensure compliance with legal and industry requirements, reducing the risk of fines and legal consequences for the company. - Company reputation preservation
Systematic monitoring and incident response allow blue teams to minimize damage from potential attacks, positively affecting the company's overall reputation. - Staff training and education
Blue teams develop and conduct educational programs, improving cybersecurity hygiene among employees and reducing social engineering risks. - Business process resilience
Blue teams help maintain business process continuity, even under attack conditions, ensuring stable revenue and customer trust.
Overall, blue teams cover everything from strategic planning to operational implementation of cybersecurity. This reduces the threat level and creates a resilient environment where businesses can operate with minimal risks and maximum efficiency.
Challenges in working with blue teams
Working with blue teams, like with red teams, offers not only a range of advantages but also certain challenges that can be critical for successful business operations.
Business process integration
Blue teams may need help integrating their methodologies and tools into existing business processes, requiring additional resources for adaptation.
Staff training
Implementing new security technologies and methods requires additional employee training, which can slow down the implementation process and increase costs.
Technical limitations
Not all systems and applications can be fully secured due to outdated hardware or software, creating additional risks.
Coordination complexity
Working with external blue teams can lead to communication and coordination issues, especially if the team and the company have different approaches to security.
Result validation complexity
Assessing the effectiveness of security measures can be a complex task requiring specialized tools and methodologies, increasing both time and financial costs.
Risk of system overcomplication
Blue teams may overload the system with excessive measures and controls to maximize security, potentially reducing performance and ease of use.
Need for constant updates
Technologies and methods quickly become obsolete, requiring constant updating and adaptation, which can be resource-intensive and require additional investments.
In conclusion, effective collaboration with blue teams requires a comprehensive approach, including business process integration, staff training, and technical adaptation. Managing these and other complexities will allow your company to maximize the effectiveness of developed and implemented security measures while minimizing risks and costs.
Market data on demand, capitalization, and trends for red and blue teams
According to Fortune Business Insights, the current cybersecurity market valuation stands at $172.32 billion. This figure is not just impressive; it reflects the growing dependency of businesses and governmental structures on digital technologies. The market is projected to reach $494.37 billion by 2030 with a CAGR of 13.8%, and several key trends drive this growth.
Firstly, the increase in the number of devices connected to the internet, and consequently, the expansion of the landscape for potential cyberattacks. This will necessitate an increasingly diverse range of specialists and more versatile teams to provide comprehensive protection for organizations. Secondly, with the increasing complexity of cyber threats, old protection methods are becoming ineffective, requiring more complex approaches and technologies and the collaborative work of multiple teams addressing security from various angles.
Best practices for working with red and blue teams
Knowing the growing importance of cybersecurity, you may wonder if there are specific practices that can help avoid the complexities we discussed earlier when working with red and blue teams. Here are the main ones.
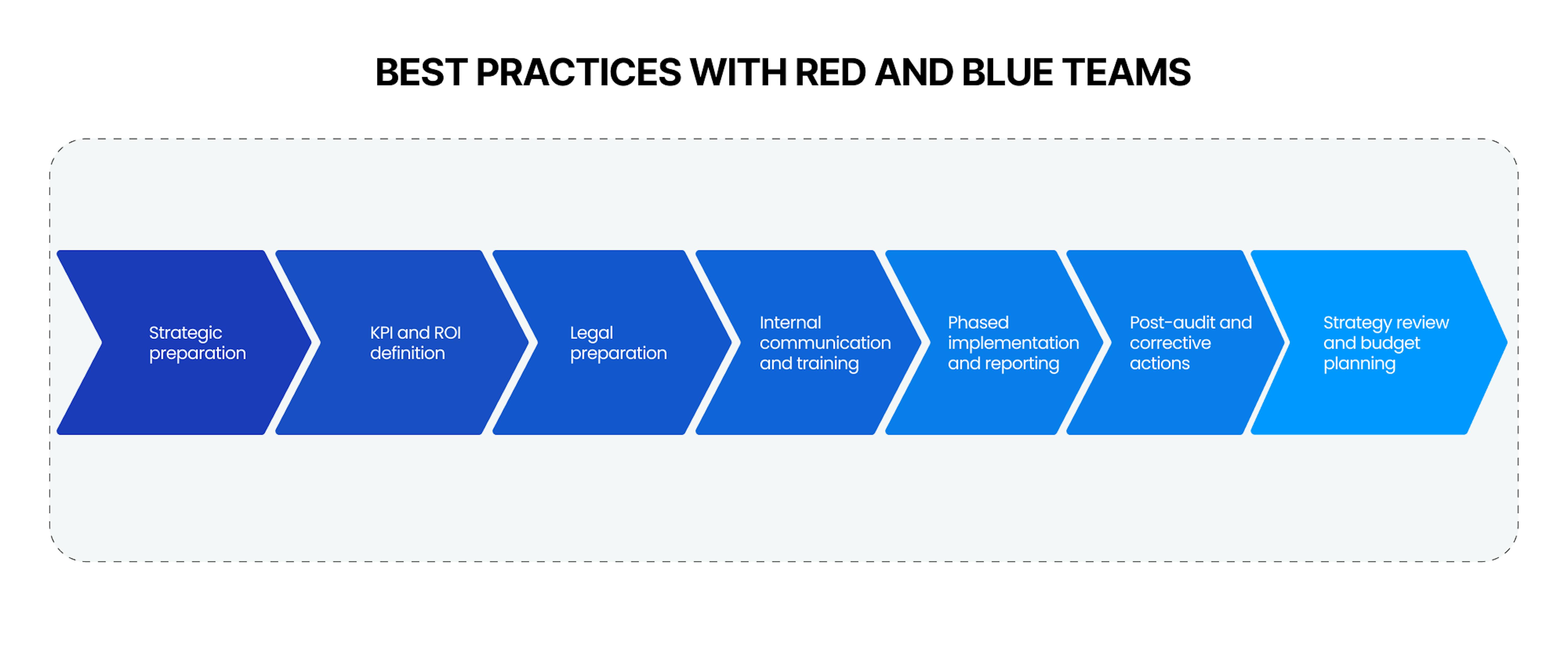
Strategic preparation
This is a foundational stage that determines the entire project's success. Conduct an audit of all digital assets using automated tools and manual analysis. Create a risk matrix for each asset, which is key for budget and timeline determination. These parameters should be agreed upon with the finance department and approved at the management level.KPI and ROI definition
KPI and ROI are absolutely necessary to evaluate effectiveness and justify expenditures. Use specialized tools for monitoring KPIs, such as project management systems or dashboards. Regular ROI analysis, comparing costs and outcomes, will allow real-time strategy adjustments.Legal preparation
Legal preparation is not just a formality; it protects your company's interests. Consult with lawyers on cybersecurity issues and prepare NDAs and other legal documents. Remember to get cyber risk insurance to minimize financial losses.Internal communication and training
This stage is more than keeping everyone informed but also about establishing a cybersecurity culture within the company. Organize regular training sessions and webinars and implement a knowledge management system for storing and accessing materials.Phased implementation and reporting
The phased implementation helps avoid chaos and inefficiency. Develop a detailed implementation plan broken down into stages and set up reporting mechanisms at each stage. This ensures transparency and the possibility for adjustments if needed.Post-audit and corrective actions
The post-audit is not the end; it's a new stage for improvement. Conduct an audit using external and internal resources, analyze the results, and develop a corrective action plan. This will not only eliminate vulnerabilities but also optimize processes.Strategy review and budget planning
Strategy review is an opportunity for growth and optimization. Regularly analyze current KPIs and ROIs and adjust the strategy and budget based on the analysis. This ensures the sustainability and effectiveness of your cybersecurity measures.
Careful attention and thoughtful application of these practices will significantly help save costs, reduce potential risks, and maximize the benefits of working with red and blue teams, allowing your business to always be ready for new challenges in a constantly changing digital environment.
Summary
By now, you should have a comprehensive understanding of the roles of red and blue teams in cybersecurity, specifically their areas of expertise and the specific methods and approaches for testing and ensuring security. We described their importance in the security of organizations, from small to transnational, from commercial to governmental, and how this importance grows each year. Additionally, we laid it out that with red and blue teams, aside from the direct benefits each brings, also comes with complexities that require appropriate attention and approach.
If you have more specific questions or a particular need for a security assessment of your systems and the safeguarding of your business processes and assets, feel free to reach out for a free consultation with our experts. We will carefully consider your request, considering all your business features and capabilities, and offer the best-proven practices and most advantageous solutions.












Social engineering