Cybersecurity is a rapidly evolving discipline that eagerly assimilates cutting-edge technologies, fortifying them into a robust shield for our peaceful existence, largely unnoticed by the majority. However, for those with less noble intentions, these technologies become a sword aimed at disrupting the tranquility and confidence in the future for entire companies and the people reliant on them.
Hence, adhering to and assessing compliance with modern cybersecurity practices is crucial. Utilizing advanced tools is paramount to ensuring security, considering all potential risks today, and minimizing their probability to an absolute minimum.
In this article, you will discover the critical steps in risk assessment and the pivotal role each plays. Additionally, we'll explore various risk management strategies based on an organization's position or the situation it finds itself in. You'll also gain insights into the best industrial practices and tools for cybersecurity risk assessment and management, understanding their goals, features, and limitations.
Key risk assessment and management strategies
In cybersecurity, various strategies empower organizations to navigate and manage risks effectively and aim to find an individual balance between ensuring security and allocating your organization's resources. Let's explore the most prevalent ones.
Risk acceptance
Organizations may consciously embrace specific risks in certain scenarios to sustain their business processes. This involves a meticulous evaluation and understanding of risks, culminating in the decision that the potential benefits of maintaining the current state outweigh foreseeable threats. Risk acceptance demands thorough analysis, considering how the risk aligns with the organization's goals and strategy.
A preferred approach is to eliminate risk entirely by devising and implementing a plan that minimizes the likelihood of threats. This encompasses altering business processes, technological systems, or organizational principles to eradicate certain types of risks. Risk avoidance necessitates strategic planning and an analysis of how changes impact the overall structure of the enterprise.
Risk transfer
Frequently, a more cost-effective and dependable strategy involves delegating the responsibility for risk management to a third party. This may encompass entering into insurance contracts or other agreements where a third party assumes certain aspects of the risk. This approach is particularly effective when the organization lacks the resources or expertise to manage specific risks effectively.
Risk mitigation
This strategy involves taking specific measures to reduce the impact of known risks on the organization, which is nearly impossible to eliminate completely. Measures can span technological solutions, such as implementing secure practices, data encryption, or reinforcing network defenses, to organizational changes, including staff training, establishing clear procedures, and routinely testing security systems. Risk mitigation aims to forge a more resilient and secure environment for the organization.
🛡️ Learn about the potential devastation of a cyber attack on small businesses and why investing in cyber liability insurance is crucial for SBMs in our new article.
Cybersecurity risk assessment practices
It is essential to undertake a series of fundamental steps in assessing risks themselves to determine the most fitting risk strategy for your organization.
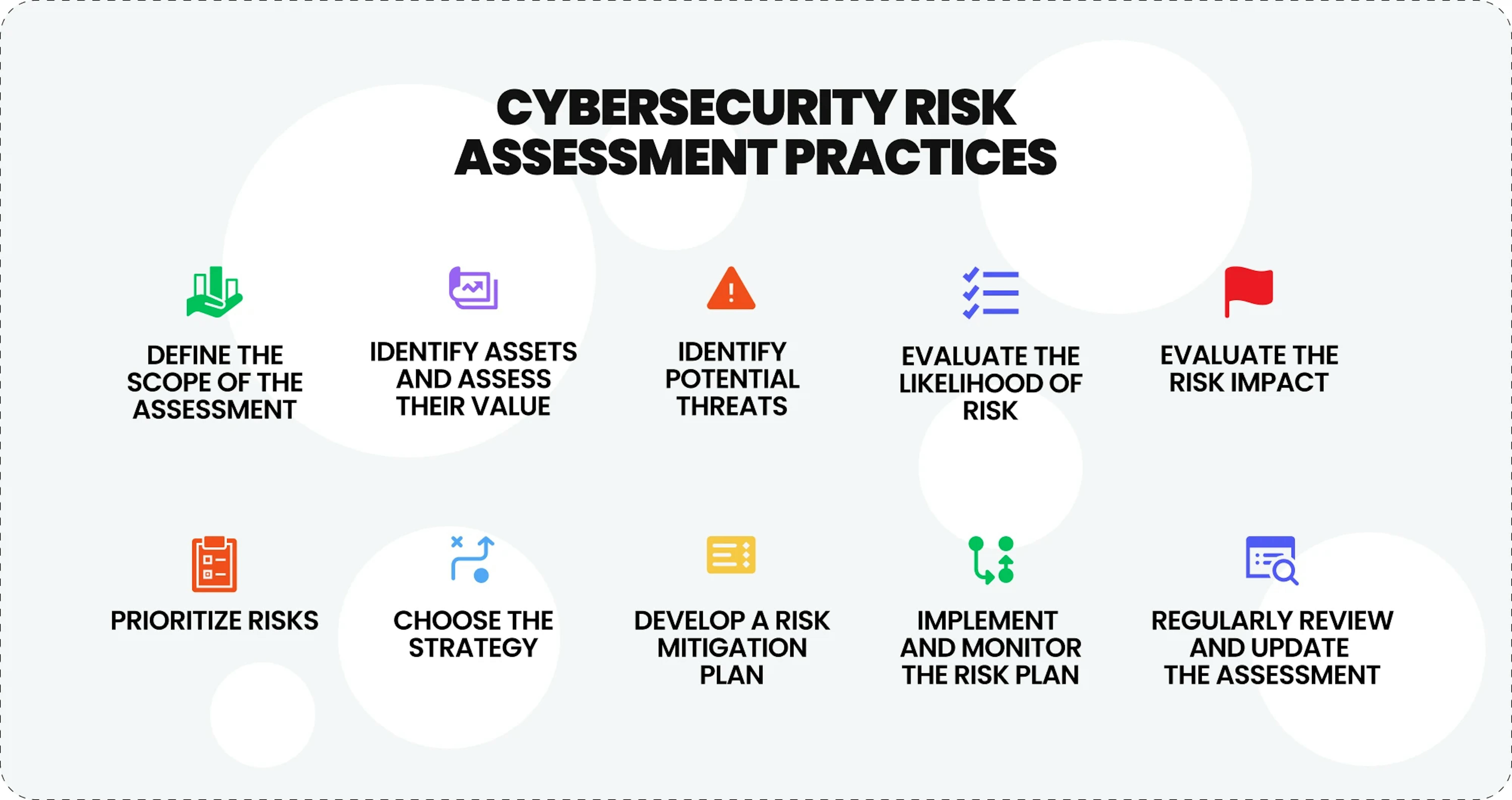
Define the scope of the assessment. It is important to clearly define the systems, assets, and data that will be included in the assessment. This helps to ensure that the assessment is comprehensive.
Identify assets and assess their value. Recognize assets within the assessment's scope and determine their importance, including everything regarding its contribution to the organization's overall operations.
Identify potential threats. Understand potential threats that could impact the assets. This should be based on reviewing current and historical threat information and analyzing the potential for new or emerging threats.
Evaluate the likelihood of risk. Determine the likelihood of each risk occurring. This should be based on the available information and considering the current threat landscape.
Evaluate the risk impact. Consider the impact of each identified risk on the assets and overall operations of the organization if it were to occur. This should consider the consequences of a breach and the extent of the damage that could be caused.
Prioritize risks. Based on the likelihood and impact of each identified risk, prioritize all of them, from the more and less significant ones, and which of them need to be addressed first.
Choose the strategy. Once all risks have been considered and prioritized for your individual case, you need to choose the most appropriate strategy that will not require excessive resources from you and will be consistent with the goals and features of your organization.
Develop a risk mitigation plan. Build a detailed plan that brings your chosen strategy to life. This should include specific actions, responsibilities, and deadlines for each risk handling.
Implement and monitor the risk plan. Your plan should then be implemented and monitored to ensure that it effectively handles each particular risk. This may involve regular monitoring and updating the plan as the threat landscape changes.
Regularly review and update the assessment. It is important to ensure that organization security measures remain current to protect against cyber threats. This should include regular assessments of the threat landscape and the effectiveness of the overall risk management strategy.
You will find these fundamental practices in each cybersecurity framework in one way or another, but they will be more specific regarding each framework's approach. Its variety is needed to give the most concrete and detailed controls that enable each individual organization to handle its security issues properly.
Cybersecurity risk assessment frameworks and controls
The best global practices in cybersecurity risk assessment result from years of collaboration among numerous security experts, and their value is immeasurable. Each addition to these practices is driven by real security incidents, posing threats to individual companies or entire nations.
➡️ These practices are systematically compiled in various frameworks, with ISO/IEC 27001 and NIST being the most globally recognized. For a more detailed understanding of these frameworks' crucial role in ensuring cybersecurity, you can explore our comprehensive article, "Cybersecurity Risk Assessment: Market Share and Industry Standards."
However, a few more frameworks encompass crucial practices significantly enhancing cybersecurity risk assessment and management, and implementing them elevates the security level of your organization.
NIST. The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a set of standards and guidelines for organizations to manage and reduce cybersecurity risk. It provides a common language for organizations to describe and prioritize their security risks and develop a risk management plan. The framework is based on five core functions: Identify, Protect, Detect, Respond, and Recover.
ISO/IEC 27001. The standard provides a systematic approach to managing and protecting sensitive information. It outlines a set of best practices for information security management and provides a framework for organizations to implement, monitor, and maintain their information security management system (ISMS).
FAIR. The Factor Analysis of Information Risk (FAIR) framework is a distinctive risk management approach. It helps articulate and quantify organizational information risks, facilitating well-informed decisions in risk management. Unlike traditional approaches, FAIR provides a nuanced understanding of risk factors, enabling organizations to tailor their risk management strategies with a high degree of precision.
CRISC. The Certified in Risk and Information Systems Control (CRISC) certification is crafted for IT professionals who manage and mitigate information security risks and provide a deep understanding of risk management best practices, fostering the skills needed for effective decision-making in the dynamic realm of information security. CRISC emphasizes practical applications, ensuring professionals are adept at addressing real-world challenges in the evolving cybersecurity landscape.
Top cyber risk assessment tools
Making a detailed plan, manually applying it, and tracking it can take enormous resources. So, there are sets of ready-made solutions to largely automate and optimize this process and make it more cost-effective and high-performance.
➡️ Of course, a lot still needs to be done manually. For example, although we successfully automate testing, many continue to use manual testing. To understand why this happens and which testing method is better, read our article on "Vulnerability Assessment vs Penetration Testing."
Now, let's take a closer look at the best tools to help with cyber security risk assessment.
CyberArk

CyberArk is a widely recognized solution for privileged access management and security. Its robust features and effective scalability make it a preferred choice for large and medium-sized enterprises with complex privilege management needs.
Features
- Privileged account management (PAM). Comprehensive PAM functionality, providing secure management and monitoring of privileged accounts.
- Endpoint privilege management. With granular control, organizations can manage endpoints' privileges, mitigating the risk of unauthorized system access.
- Credential vaulting. It excels in the secure vaulting and management of credentials to protect sensitive information against potential breaches.
- Session monitoring and recording. Robust session monitoring and recording capabilities, empowering organizations to trace and audit privileged activities.
- Behavioral analytics. Detecting unnatural patterns adds a layer of protection by proactively identifying potential security threats.
- Comprehensive auditing. The platform facilitates detailed auditing, giving organizations a transparent view of privileged access activities and contributing to compliance efforts.
SecurityScorecard

SecurityScorecard is a cutting-edge cybersecurity rating platform that helps organizations gain insights into their security standing through continuous evaluation. Its features, including a dynamic rating system, continuous monitoring, industry benchmarking, and assessment of third-party vendor cybersecurity, make it suitable for medium and large companies aiming for active cybersecurity management in a dynamic environment.
Features
- Dynamic letter-grade rating. SecurityScorecard distills intricate security metrics into a transparent and easily understandable format.
- Real-time vigilance. With a commitment to continuous monitoring, it provides organizations with up-to-the-minute updates on their security status, enabling swift responses to evolving threats.
- Precision benchmarking. Organizations can gauge their security posture against industry benchmarks, gaining strategic intelligence to drive targeted improvements.
- Holistic third-party risk assessment. It enables the assessment of third-party vendors' security resilience, empowering organizations to manage external risks proactively.
- Strategic incident response planning. A comprehensive and continuous analysis of potential risks makes it much more handy to prepare a security incident strategy.
- Incorporating threat intelligence. By integrating the latest threat intelligence models, it remains at the forefront of cybersecurity trends, enhancing its ability to identify and evaluate emerging risks.
Microsoft Threat Modeling Tool

Microsoft Threat Modeling Tool provides capabilities for analyzing and modeling threats in applications. Developed by Microsoft, it is highly adaptable in companies of any size, but with its accessibility, it is also attractive to small and medium-sized enterprises.
Features
- Visual insight into threats. Central to its functionality is providing a rich visual representation of potential threats, granting developers a profound understanding of security vulnerabilities within software architectures.
- Seamless integration. It integrates into the software development processes and becomes an intrinsic part of the workflow, embedding security considerations right from the project's initiation.
- Proactive risk mitigation. Enables developers with visualization and analysis of potential threats and facilitates proactive measures, resulting in more robust, productive, and secure software development.
- Comprehensive security planning. Facilitate comprehensive security planning throughout the software development lifecycle and ensure that security is a fundamental aspect rather than an afterthought.
- Tailored security insights. Developers benefit from customizable insights into potential security threats, allowing for bespoke solutions that align with the unique characteristics of the software under development.
- Real-time collaborative environment. Supports real-time collaboration between development and security teams, cultivating an environment where security is a shared responsibility.
- Documentation excellence. Facilitate the creation of comprehensive documentation and enable security considerations to be well-documented and easily accessible for future reference.
Tenable.io

Tenable.io is a cloud-based platform for vulnerability management and cyber exposure, offering organizations a comprehensive and adaptive approach to cybersecurity. Its scalability, extensive analytical capabilities, and ability to accurately identify assets make it most suitable for medium and large organizations with high cybersecurity requirements and complex network structures.
Features
- Uninterrupted monitoring. Tenable.io is also robustly committed to continuous monitoring, ensuring organizations maintain a proactive defense against ever-evolving cyber threats.
- Precise asset identification. The platform excels in identifying and cataloging assets, providing organizations with a meticulous inventory crucial for effective security management.
- Sophisticated analytics. It enables leveraging advanced analytics for vulnerability detection, furnishing organizations with nuanced insights for precise risk assessment.
- Strategic risk prioritization. The platform prioritizes risks strategically, empowering organizations to channel resources towards promptly addressing the most critical vulnerabilities.
- Transparent reporting. It generates detailed and transparent reports, providing organizations with the essential information for strategic decision-making and regulatory compliance.
- Adaptable scalability. Engineered with adaptable scalability, it meets the intricate security needs of large enterprises, delivering tailored and effective cybersecurity solutions.
Qualys

Qualys stands at the forefront as a cloud-based security and compliance platform. It offers a comprehensive set of tools for vulnerability scanning and network security. Due to its scalability and high performance, it is a good choice for medium to large companies.
Features
- Cloud-first security paradigm. Qualys pioneers a cloud-centric approach, providing organizations with the agility of cloud-based solutions for heightened accessibility, scalability, and adaptability.
- Dynamic real-time insights. The platform delivers dynamic real-time insights into an organization's security posture, enabling swift responses to emerging threats and vulnerabilities.
- Comprehensive vulnerability management. It excels in vulnerability management, addressing various security issues and fostering a proactive defense against potential risks.
- Strategic asset management. With a dedicated focus on asset management, it enables a comprehensive inventory of assets, facilitating effective resource allocation for enhanced security.
- Holistic policy compliance assessments. Qualys provides functionality that comprehensively assists organizations in aligning their security practices with industry and regulatory standards.
- Enterprise-grade scalability. It caters to the complex needs of large enterprises, engineered for enterprise-grade scalability, providing a robust and scalable cybersecurity framework tailored to organizational intricacies.
- Continuous monitoring vigilance. The platform adopts a continuous monitoring approach to stay ahead of dynamic cyber threats and maintain persistent security vigilance.
- Detailed actionable reporting. It generates detailed reports, furnishing organizations with clear information for precise audits and compliance adherence.
Nessus

Nessus is a cybersecurity pioneer, introducing an extensively adopted vulnerability scanner. It is known for its flexibility and accessibility, and provides rich vulnerability detection and management capabilities even in free versions. That makes Nessus preferable for organizations of various sizes, including small and medium-sized enterprises.
Features
- Exhaustive vulnerability analysis. Nessus distinguishes itself with thorough vulnerability analyses, furnishing organizations with a nuanced understanding of potential security weaknesses within their systems and networks.
- Tailored scanning solutions. Offering the flexibility of customizable scanning, it empowers organizations to tailor scans based on specific needs, optimizing the efficiency of vulnerability identification.
- Dynamic asset discovery. It enriches its offerings with dynamic asset discovery, delivering a comprehensive inventory crucial for organizations to manage their security resources effectively.
- Holistic compliance checking. The platform extends its capabilities to comprehensive compliance checking, ensuring strict adherence to industry standards and regulatory requirements, forming the bedrock of a resilient security framework.
- User-friendly interface. It prioritizes user accessibility with an interface designed for ease of use, democratizing the intricate task of vulnerability scanning for security professionals across various expertise levels.
- Timely updates. It stays abreast of evolving threats through regular updates, assimilating the latest threat intelligence to enhance scanning capabilities and deliver accurate, up-to-date results.
- Seamless Integration. Nessus seamlessly integrates into diverse IT environments, fostering interoperability with other security solutions and contributing to a unified and cohesive cybersecurity strategy.
Depending on your industry, company, and budget, you can find the most beneficial tools and combine some of them.
Summary
The cybersecurity landscape constantly evolves, with changes happening increasingly rapidly and risks becoming more diverse. Therefore, continuous reassessment and updating of cybersecurity are critical for the success of any organization.
Today, have gained insights into the fundamental risk management strategies and the key steps required to determine which is most applicable to your organization.
You have also learned the best practices to consider for a thorough risk assessment and the tools that can automate and enhance the evaluation and support of cybersecurity-related risks.
If your business requires additional assistance in cybersecurity assessment or in implementing and developing customized systems to ensure security, contact our experts for a free consultation. We will carefully analyze your business and assist you in finding the most effective and cost-efficient personalized solution.










