A growing number of organizations are looking closely at cybersecurity-as-a-service — an outsourced model for managing risk on a pay-as-you-go basis. This approach offers a cost-efficient, adaptable, and expandable means to handle cybersecurity threats, enabling businesses to concentrate on their primary operations.
In this article, you will learn:
- What is cybersecurity-as-a-service, and what is the difference from traditional cybersecurity? And what benefits can it provide?
- What types of cybersecurity-as-a-service companies are out there? What are their top services?
What is cybersecurity-as-a-service
Cybersecurity-as-a-service (CSaaS) is a model where organizations subscribe to or outsource their cybersecurity needs to a third-party service provider. In this model, the service provider delivers a range of cybersecurity services, tools, and expertise to help protect an organization's digital assets and information systems from cyber threats and vulnerabilities.
CSaaS encompasses various critical security elements to ensure comprehensive protection for organizations. These elements include:
Application security. Protection of sensitive credentials and applications from email-based attacks is part of this process.
Endpoint security. It extends beyond traditional firewalls to include securing conthat nected devices that remote workers use. This ensures that devices outside the corporate network are protected against potential threats.
Data security. CSaaS focuses on securing data when it is in motion (being transferred) and at rest (stored). As a result, data remains protected throughout its lifecycle.
Network security. CSaaS includes measures to filter out harmful traffic and block potential intruders from accessing the network. By doing so, the integrity and confidentiality of the network infrastructure can be maintained.
Cloud security. CSaaS covers security measures for multi-cloud environments, ensuring that data and applications hosted in the cloud are protected against unauthorized access and other potential threats.
Managed detection and response (MDR). CSaaS providers offer MDR services, which involve actively monitoring systems and networks for any signs of threat activity. If a threat is detected, the provider will respond quickly to neutralize it.
Discover why 41% of small businesses faced cyber attacks and learn how cyber liability insurance can shield your business from devastating repercussions.
➡️ Discover now
How does cybersecurity-as-a-service differ from traditional cybersecurity
Managing cybersecurity in-house is challenging, especially with digital transformation and IoT. As businesses go digital, the attack surface grows. Meeting the security expectations of both employees and customers is crucial.
Traditionally, the construction of an internal security team involves hiring experienced professionals dedicated to creating and enforcing a company-wide security strategy tailored to the organization's needs. However, this approach can be resource-intensive and time-consuming, especially for larger enterprises with extensive staff and systems spread across multiple locations. As organizations grow, in-house security efforts can strain available resources.
CSaaS provides an outsourcing alternative. Some companies prefer a comprehensive approach, where they partner with a single vendor to handle all their security needs. Others delegate specific enterprise security functions either partially or entirely to external providers. Some organizations take a more flexible approach to CSaaS, opting to outsource certain aspects to a vendor while retaining others in-house.
How does cybersecurity-as-a-service work
CSaaS integrates top-tier security services, software, and human expertise into a comprehensive solution.
At the core of every CSaaS provider is their security operations center (SOC), a cutting-edge facility dedicated to monitoring and addressing security threats for your organization. These SOCs are typically staffed by experienced security professionals committed to monitoring, identifying, tracking, and resolving security incidents. They leverage high-level security software and advanced tools to detect and prioritize system threats.
Within the CSaaS framework, the SOC utilizes technology and human knowledge to oversee your business systems for security risks. This approach may encompass cutting-edge technologies like artificial intelligence (AI), managed detection and response (MDR), managed incident response, endpoint security, application security, data security, and cloud security. SOC teams may also proactively hunt for potential threats using diverse methods, including social media monitoring, dark web intelligence, and open-source intelligence.
Organizations eliminate the need to establish their security tools and processes by opting for cloud-based or subscription-based CSaaS. Some managed security providers can initiate environment monitoring within days or weeks, ensuring proactive protection and peace of mind more rapidly than traditional in-house security models.
What benefits can CSaaS provide
Some key benefits of CSaaS include:
Cybersecurity resources are managed centrally
CSaaS simplifies cybersecurity resource management by enabling organizations to oversee and prioritize their cybersecurity efforts from a single, convenient location.Scalability
Today's businesses adapt to a dynamic global economy, causing cybersecurity needs to shift over time. CSaaS offers flexibility, enabling organizations to optimize resource allocation and avoid overspending on unnecessary features.Detection and response capabilities are automated
CSaaS platforms often include automated threat detection and response capabilities, enabling swift actions against cyber threats, reducing the impact of attacks, and safeguarding critical data.Integrated security solutions
Numerous CSaaS platforms offer integrated security solutions, simplifying the deployment of comprehensive cybersecurity strategies to protect all systems. It is a valuable tool for businesses seeking enhanced cyberattack protection, with various options available to meet specific organizational requirements.
What types of cybersecurity-as-a-service companies exist
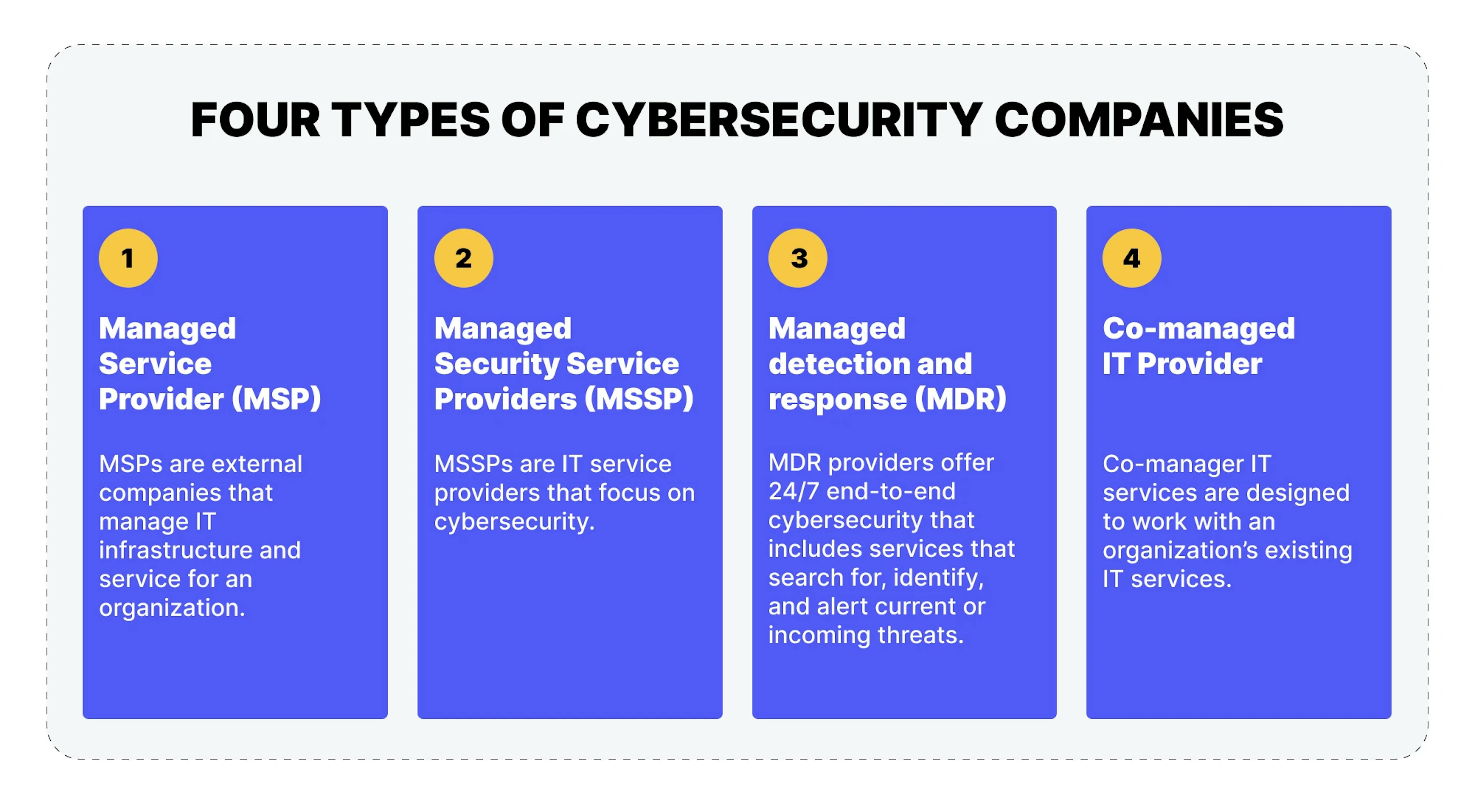
Running an in-house SOC is often too complex and costly for many companies. Managed cybersecurity services from specialized companies offer similar protection at a much lower cost. However, it is essential to recognize that cybersecurity services can differ among providers. By understanding the common categories of cybersecurity vendors and managed security service companies, you can better assess your specific cybersecurity requirements.
MSPs
Suitability: For companies of various sizes, it offers comprehensive tech infrastructure management, cybersecurity services, and network security components.
Managed service providers (MSPs) are external companies overseeing an organization's tech infrastructure and services. They typically include various network security components within their services, which play a crucial role in managing the structural aspects of your cybersecurity solution. This includes firewall management, email security, sandboxing, data loss prevention, and access control. MSPs also handle tasks such as updates and patches to address potential vulnerabilities. It is worth noting that traditional MSP services primarily focus on on-premises network cybersecurity, and they generally do not have an off-site SOC to assist.
MSSPs
Suitability: Suitable for small to large companies, especially those lacking dedicated in-house cybersecurity teams. Provides a comprehensive security approach.
Managed security service providers (MSSPs) are specialized tech service providers primarily focusing on cybersecurity. They deliver comprehensive network security monitoring and management services that cover an organization's entire tech environment. Many MSSPs offer 24/7 network monitoring, along with additional services like vulnerability management and security configuration. Common services provided by MSSPs include managed firewall services, intrusion detection, virtual private network management, vulnerability scanning, antivirus services, and security information and event management (SIEM) monitoring.
MDRs
Suitability: Suitable for companies of all sizes, it provides proactive threat detection, incident response, and cybersecurity expertise to enhance security.
Managed detection and response (MDR) is a comprehensive 24/7 cybersecurity solution that actively seeks out, identifies, and promptly alerts organizations about existing or incoming threats. While MDR and managed security service providers (MSSP) offer cybersecurity services with various tools and features, MDR is inherently more proactive. It leverages cutting-edge technologies to combat modern cyber threats, utilizing integrated tools for proactive threat detection, hunting, and response. MDR is staffed by real experts, with live threat hunters continuously monitoring client networks in real time to identify indicators of attack and compromise. One of the key services MDR providers offer is extended detection and response (XDR).
Co-managed tech service providers
Suitability: Suits companies of varying sizes and offers flexibility and specialized expertise to complement internal tech teams or address specific tech needs.
Co-managed tech service providers collaborate with an organization's existing tech services. They rely on the internal tech team's expertise to deliver supplementary services that help the organization bridge potential security gaps. Organizations with in-house solid tech teams can benefit from tailored co-managed services that maximize the combined knowledge of both teams. These services can encompass a range of offerings, from co-managed security information and event management (SIEM) to security operations center as a service (SOCaaS).
How much do cybersecurity-as-a-service provider's services cost
On average, consider allocating 5.6% to 20% of your budget to cybersecurity. Depending on your company size or specific services, costs may differ.
Outsourced cybersecurity services generally start at a minimum cost of $2,000 to $3,500 monthly. On a per-user basis, this equates to a range of $195 to $350 per user, covering support and maintenance. If you already have support, the standalone cybersecurity cost is typically $35 to $65 per user.
In the third quarter of 2022, there was a 28% increase in worldwide cyberattacks, and the average expense of data breaches rose by 12.7% compared to 2020, reaching $4.35 million. These services play a crucial role in protecting sensitive information, preventing substantial penalties and ransom costs, as well as mitigating long-term reputational harm. Additionally, they assist in establishing proactive security initiatives, ensuring adherence to regulations, and effectively addressing cybersecurity incidents.
What questions should you ask when choosing a CSaaS provider
In more precise terms, what key factors should you emphasize when evaluating your alternatives to guarantee that a vendor is well-suited for your organization and possesses the capability to ensure your security?
Consider the following questions when evaluating a provider:
What security services does the CSaaS provider offer, and do they align with our specific security needs and requirements?
Ideally, the provider should offer a detailed list of the security services they offer and demonstrate how each of these services aligns with your specific security needs and requirements. They should be able to explain how their services can address the unique challenges of your organization.What is the provider's track record in delivering security services and their experience in our industry?
Information about the provider's track record in providing security services should be easy to access. They should offer examples of their experience in your industry, including relevant success stories and case studies.Can the provider demonstrate their compliance with relevant security standards and regulations?
The provider should present evidence of their compliance with security standards and regulations that are relevant to your industry. They should also list any certifications they hold.How does the provider handle data privacy and protection, and what measures are in place to safeguard our sensitive information?
The provider should describe their data privacy and protection practices. This description should include how sensitive information is handled, the encryption methods they employ, and the safeguards they have in place.Does the provider offer scalability to accommodate our future growth and evolving security needs?
The provider should present a scalable solution that can accommodate your future growth and evolving security needs. Request details on their scalability features and how they address rapidly changing requirements.What is the pricing structure, and does it fit within our budget constraints?
Ensure that the provider offers you a transparent pricing structure that fits your budget. They may offer different pricing options or customization to meet your financial needs.Are there references or case studies that showcase the provider's successful implementations?
References or case studies demonstrating successful implementations in similar organizations or industries must be provided by the provider. It helps validate their capabilities.How does the provider stay updated on emerging security threats and technologies, and what proactive measures do they take to mitigate risks?
The provider should describe their methods for staying updated with emerging security threats and technologies. They should also detail the proactive measures they take to mitigate risks and enhance your organization's security posture.What is the provider's approach to continuous monitoring and improvement of their security services?
Providers should explain their approach to continuously monitoring and improving your security environment. This demonstrates their commitment to keeping your security up to date.
Top cybersecurity as a service providers
Palo Alto Networks

Headquarters: Santa Clara, California
Founded: 2005
Annual revenue: $5.5 billion
This provider offers solutions for all types of companies.
Palo Alto Networks (PANW) has a longstanding record of achieving top scores in rigorous independent security evaluations. Whether in the realm of next-gen firewalls (NGFW), endpoint detection and response (EDR), or other security domains, PANW consistently excels. While the company is primarily recognized for its comprehensive cybersecurity solutions, it also demonstrated its capabilities in managed security services, securing a top 4 position in the inaugural MITRE managed security tests.
PANW's security products consistently receive high marks. This impressive track record has garnered the attention of cybersecurity buyers. Despite achieving over $5 billion in revenue, Wall Street analysts forecast a remarkable 27% annual revenue growth for this 17-year-old Santa Clara-based company over the next five years.
One of PANW's high-profile projects is setting a new standard in World Cup Qatar 2022 infrastructure at every level. The World Cup committee has installed state-of-the-art cybersecurity measures for the tournament stadiums, covering areas such as IoT, stadium Wi-Fi, industrial control systems, and cybersecurity operations. They have worked with Palo Alto Networks to ensure the implementation of behavior-based endpoint protection, threat intelligence management, and incident response.
Fortinet

Headquarters: Sunnyvale, California
Founded: 2000
Annual Revenue: $4.4 billion
This provider offers solutions for all types of companies.
The Fortinet Security Fabric encompasses FortiGuard AI-driven security, secure networking, zero trust access, and cloud security. The company has catered to more than 635,000 customers with a rich history spanning over two decades. They are renowned for delivering "real-time threat intelligence that drives action" and for their extensive expertise in networking and security.
As part of the Fortinet Security Fabric, Grey County leveraged Fortinet's AI-driven security, including FortiGate NGFW, FortiSIEM, and FortiEDR solutions. This allowed them to enhance their security posture, achieve automated threat response, and implement a zero-trust network access model. Grey County benefited from Fortinet's extensive experience in networking and security, which has been trusted by over 635,000 customers for over two decades, making its data protection and visibility enhancements a strategic choice.
Cisco

Headquarters: San Jose, California
Founded: 1984
Annual revenue: $54.5 billion
This provider offers solutions for all types of companies.
Leveraging its strong presence in the networking industry, Cisco has expanded into neighboring markets, notably network security. Cisco's security division, a $4 billion enterprise, is experiencing robust growth at a rate of 9%, outpacing the company's overall growth. Many of Cisco's customers, especially those deeply integrated with Cisco's products, are naturally drawn to its firewall, endpoint security, and other protective solutions. With an annual revenue exceeding $50 billion, Cisco's existing customer base represents a substantial market.
For example, Cisco and the NFL have a legacy of enhancing the Super Bowl experience. They utilize Cisco security solutions for protection against phishing, malware, and ransomware while offering threat intelligence and complete network visibility. During the event, on-site support from Talos Incident Response (CTIR) and their customer experience team ensures a secure and smooth Super Bowl experience.
CrowdStrike

Headquarters: Sunnyvale, California
Founded: 2011
Annual revenue: $2.2 billion
This provider offers solutions for all types of companies.
CrowdStrike's (CRWD) robust presence in the fiercely competitive EDR market and its emergence in the XDR market bode well for its prospects. Anticipated revenue growth from $2.2 billion to $3 billion within the next year and projected annual growth of an impressive 58% over the next five years underscore the strong demand for CrowdStrike's products and services. This 11-year-old company showcased its resilience by repelling a SolarWinds-related attack, an achievement it shares with Palo Alto Networks.
Zscaler

Headquarters: San Jose, CA
Founded: 2007
Annual revenue: $1.53 billion
This provider offers solutions for all types of companies.
Zscaler has ascended a few spots on our list. Anticipating revenue of $1.53 billion for the current year and a long-term growth rate projection of 53%. Their main trends include zero trust, edge security, and secure access service edge (SASE). Zscaler has earned recognition in several categories, securing spots on our lists for SASE, zero trust, web gateway, deception tools, and SD-WAN.
For instance, in June 2022, Microsoft introduced SketchUp file support, and within approximately three months, Zscaler research efforts unveiled 117 unique vulnerabilities. As a result, Microsoft temporarily disabled SketchUp support in Microsoft 365 a year later.
💼 If you are looking for cybersecurity as a service provider, working only with small or mid-size companies, there are several companies you can consider contacting:
Sophos provides comprehensive cybersecurity solutions for businesses of all sizes, including SMBs. Their services include endpoint protection, network security, email security, and more.
This company offers various cybersecurity services, including endpoint security, cloud security, and network defense. They have solutions tailored for SMBs to help protect against cyber threats.
Check Point provides cybersecurity solutions for businesses of all sizes, including SMBs. Their services include network security, endpoint protection, and cloud security.
Conclusion
To sum up, the rise of CSaaS reflects a pragmatic shift in how organizations approach cybersecurity. This new model, distinct from traditional cybersecurity approaches, offers a more cost-effective, adaptable, and scalable approach to managing security risks. By outsourcing cybersecurity on a pay-as-you-go basis, businesses can channel their resources toward core operations while entrusting their digital defenses to specialized providers.
As organizations increasingly recognize the advantages of CSaaS, it becomes pivotal to understand the differences from traditional cybersecurity, as well as the wide spectrum of services available from various CSaaS companies. The flexibility and expertise CSaaS providers offer can be a game-changer for businesses seeking to bolster their cybersecurity posture without compromising efficiency or innovation.
In this dynamic and evolving cybersecurity landscape, staying well-informed about the potential benefits and diverse offerings within the CSaaS domain can be the key to securing your digital assets and your organization's future. If you still have questions or need any help, please contact us.








